A digital personal community, or VPN, is an important device for staying secure and safe on-line. Connecting to a VPN can preserve your looking personal and away from prying eyes, making it tougher to trace your on-line exercise.
When searching for a brand new VPN or researching the right way to optimize your service you’ll seemingly run right into a head-spinning quantity of technical jargon. Encryption this and protocol that. Even studying VPN critiques can seem to be a international language at occasions.
So that can assist you make sense of all of it, we’ve compiled a listing of the highest phrases and VPN options that everybody ought to know. Understanding the next phrases will help you extra confidently navigate the VPN atmosphere and higher perceive what a VPN supplier affords.
Further studying: The best VPN services
Custom DNS
DNS, or Domain Name System, is a manner for internet addresses to be translated into numeric IP addresses. Normally, a VPN manages DNS independently with out steering from the person. However, customized DNS is a complicated characteristic that enables customers to specify a DNS server whereas related to the VPN.
There are various explanation why one would wish to change their DNS settings, however a few of the commonest are to extend looking speeds and bypass web site or ISP censorship restrictions.
The use-cases for a customized DNS are very particular and the common VPN person received’t seemingly profit enormously from messing round with the DNS settings. However, if you happen to’re a tech-savvy person or somebody who likes to tinker, then you could discover sure advantages to customizing your DNS whereas utilizing a VPN.
Dedicated IP
Surfshark VPN affords an optionally available add-on devoted IP deal with characteristic.
Surfshark
A devoted IP is a premium add-on characteristic that many VPN providers supply to customers. If you go for a devoted IP, then the VPN will offer you a static IP deal with that’s distinctive to you, however nonetheless hides your true residence IP deal with whereas related.
While it is going to price extra cash, a devoted IP can have impactful upsides. It can extra simply unblock streaming providers because it received’t seemingly be beforehand blacklisted for being a VPN server. It can even have extra success bypassing many additional verifications, similar to CAPTCHAS, when logging in to your accounts as you received’t be mistaken for a bot.
DNS leak
As talked about above, the Domain Name System, or DNS, interprets an internet deal with right into a numeric IP addresses. This course of is normally achieved by your web service supplier (ISP), which means that they’ll be privy to each web site you go to.
When you utilize a VPN, the DNS translation course of is completed by way of the VPN as a substitute of your ISP. This is among the ways in which a VPN will help preserve your on-line actions personal. However, whereas related to a VPN there’s a probability that your DNS can leak and expose your internet looking and IP deal with.
This typically happens with an improperly configured VPN or if the VPN connection fails. During our evaluation course of right here at PCWorld, we rigorously take a look at each VPN service for any DNS leaks.
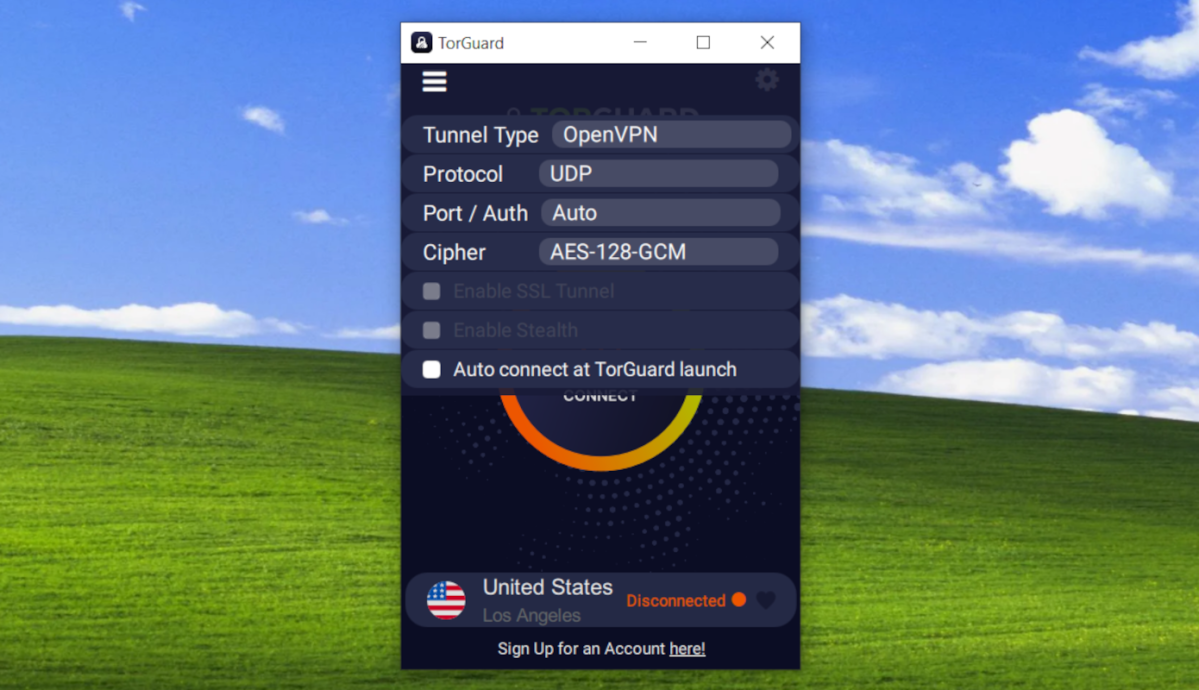
Encryption
Sam Singleton
This is the method of securely concealing information by changing it into indecipherable digital code. Once the encrypted information reaches its vacation spot, a cipher will then be used to decrypt the info. Most information despatched over the web just isn’t encrypted and thus weak to cyber threats and prying eyes.
A VPN not solely obfuscates your true connection but additionally encrypts your information whereas touring between servers. There are many several types of encryption, however VPNs will most frequently use AES-256, which is the business normal because of its “military-grade” encryption energy.
Five Eyes
Five Eyes is a global signal-sharing intelligence settlement. The members embrace the U.S., Canada, UK, Australia, and New Zealand. There are additionally different worldwide agreements similar to Nine Eyes and 14 Eyes.
If a VPN is headquartered in one in all these nations, it might be topic to data-sharing legal guidelines that might compromise a person’s privateness. Therefore, if you happen to’re involved along with your anonymity whereas utilizing a VPN, it’s a good suggestion to search for a VPN situated in a rustic exterior of the jurisdiction of those alliances.
Geoblocking
Sam Singleton
Geoblocking is the act of proscribing or limiting entry to on-line content material primarily based on a person’s residence IP deal with. This most frequently comes within the type of a streaming platform, similar to Netflix or Amazon Prime, blocking content material out of the country.
A VPN is among the finest methods to get round these restrictions so you possibly can all the time entry the content material you’ve paid for, it doesn’t matter what nation you end up in. A VPN’s capacity to entry this geoblocked content material is a vital issue to think about when in search of a superb VPN service.
Further studying: The best VPN for streaming Netflix
Kill swap
Often included with VPNs, a kill swap will minimize off your web entry must you lose connection to your VPN for any cause. This will finally stop any of your information or web site visitors from being uncovered and visual to others ought to the connection unexpectedly drop. It’s essential characteristic in any good VPN.
Logs
Various logs and information information are stored about person exercise both from an ISP or VPN service. In basic, there are two forms of logs stored by VPNs: connection logs and utilization logs.
The first, connection logs, are sometimes solely stored for shorter durations of time and permit VPNs to observe and assess server load and upkeep necessities. They are usually nameless and solely include information about connection sort, length of connection, and what gadget was used to attach with.
Usage logs are the essential bit that customers must be involved about. Most respected VPNs declare to abide by strict “no-log” insurance policies, which truly means they preserve no utilization logs. This sort of information can include personally identifiable info similar to a person’s residence IP deal with, and detailed details about their internet site visitors. When selecting a VPN make certain to search for their no-log coverage in addition to any unbiased safety audits they could have undergone to substantiate this declare.
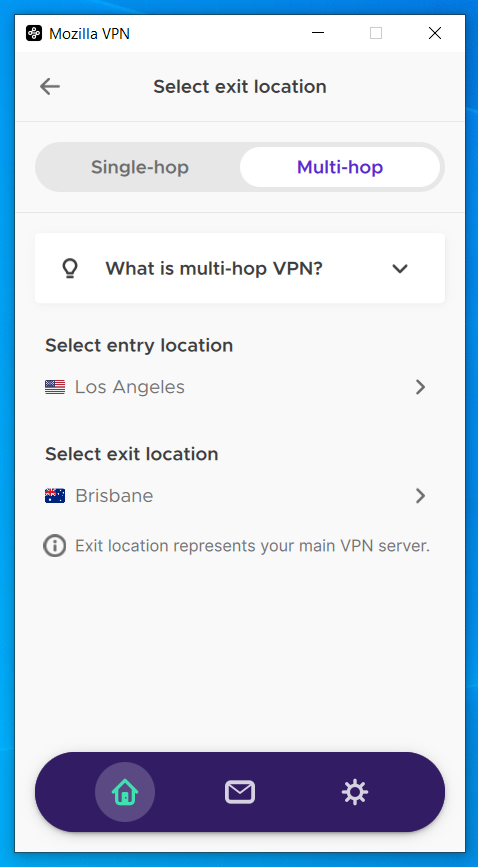
Multi-hop
Sam Singleton
Multi-hop is a relatively new characteristic for many VPN providers and also you’ll nonetheless discover many who don’t even supply it. This characteristic permits customers to route their site visitors by two or extra VPN servers relatively than simply the usual one. The aim right here is to additional obfuscate the person’s true IP deal with and add an additional layer of safety to the VPN connection.
Each successive VPN server you route by will seemingly decelerate your connection speeds even additional although. That makes multi-hop a superb choice for primary looking actions, however could hinder your capacity to sport or stream HD movies whereas related.
Further studying: How to test your VPN speed
Onion over VPN
The Tor (The Onion Router) community permits customers to securely and privately browse the web by directing internet site visitors by a number of routers, or nodes, making it troublesome to trace and determine their actions.
Using Onion over VPN merely signifies that you first hook up with a VPN server earlier than you start utilizing the Tor browser. In doing so, you add an additional layer of safety and anonymization to your connection. This is a superb safety measure as it might probably defend you from any potential threats from compromised or doubtful servers throughout the Tor community.
P2P (Peer-to-Peer)
This refers to a file-sharing community wherein two or extra events can change information with each other, relatively than by way of a centralized server. The commonest type of P2P sharing is torrenting, which is completed by way of the BitTorlease community.
Be conscious, although, that relying on the forms of information you’re torrenting, you could be violating an ISP’s phrases of utilization and will have your web connection throttled and even terminated. Many VPNs these days assist P2P sharing, so it’s extremely advisable that you just use a VPN always whereas torrenting.
Server depend/server unfold
If you hear a few VPN’s server depend or server unfold, this simply means the quantity and site of the servers in a VPN’s community. This may be wherever from a couple of hundred servers to hundreds unfold all the world over. A bigger server depend is commonly, however not all the time, a robust indication of a superb VPN service.
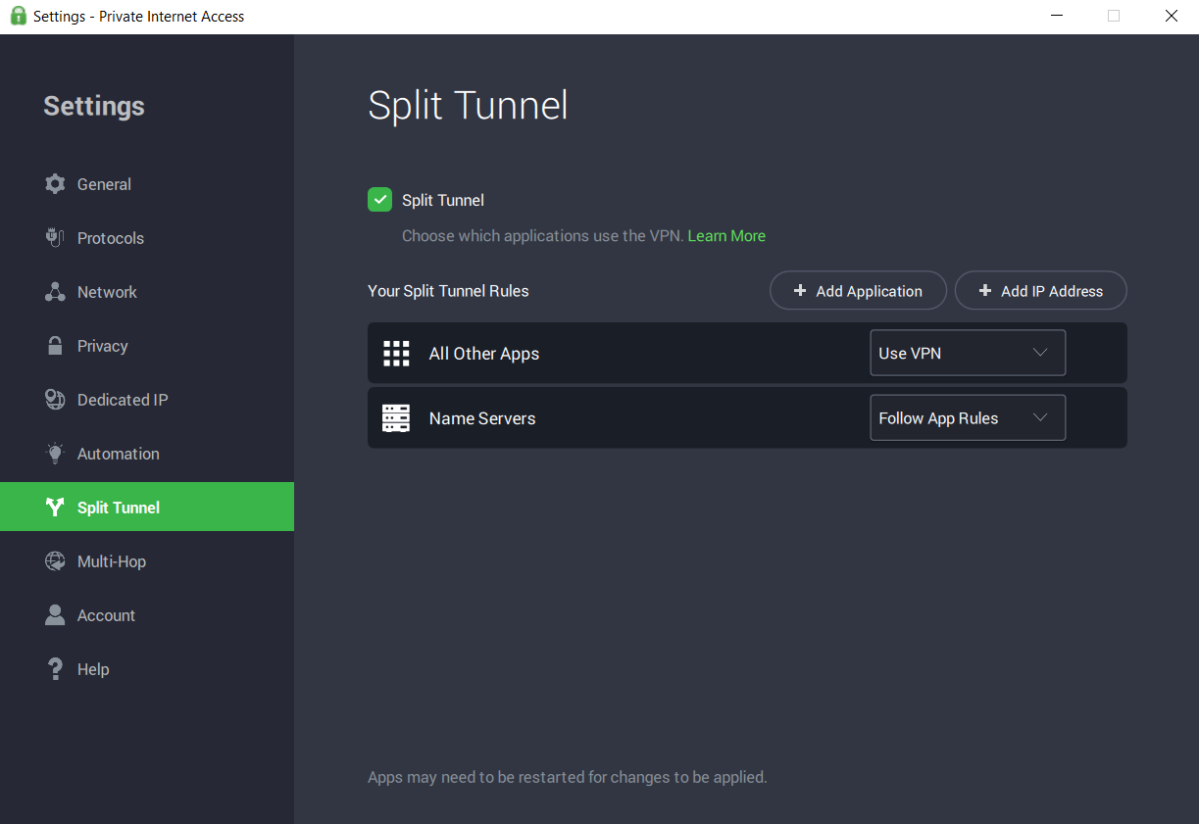
Split-tunneling
Sam Singleton
Split-tunneling is a nifty VPN characteristic that permits you to create two VPN tunnels on the identical time. This can be utilized to permit sure apps or applications to run by a VPN server whereas others keep related to their residence ISP.
There are a couple of frequent methods to make the most of this characteristic. The first is to guard your web exercise whereas looking the online with one tunnel whereas the opposite tunnel is used to guard apps in your telephone or laptop.
The second frequent method to benefit from split-tunneling is by operating your web browser site visitors by a VPN when you go away your on-line video games related to your common ISP. This manner you possibly can browse the online safely whereas holding the utmost connection velocity of your own home web.
VPN protocol
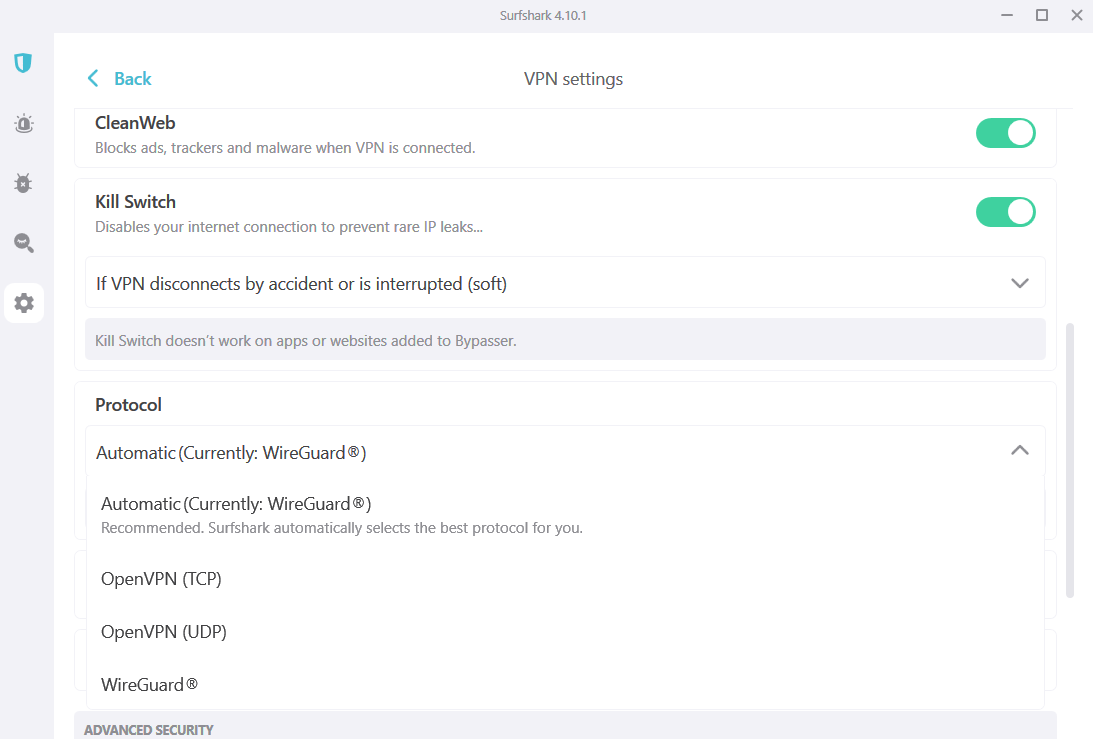
Sam Singleton
A VPN protocol is a algorithm that govern how information is encrypted and despatched between your gadget and a VPN’s server. Different protocols give attention to completely different options similar to excessive speeds, sturdy safety encryption, or community stability. However, no protocol is ideal and every has tradeoffs.
There are quite a few protocols on supply these days, however the most typical VPN protocols are OpenVPN, IPsec/IKEv2, and WireGuard. The OpenVPN protocol is a superb choice for safety and stability. IPsec/IKEv2 is decently quick and really safe, however is especially used to maintain units on the transfer safe because the VPN connection received’t drop when switching between Wi-Fi and cell information. WireGuard is the newest protocol and it’s extraordinarily quick and safe and has the additional advantage of being open supply.
At PCWorld we advocate that customers go for both WireGuard or OpenVPN as these present the perfect combination of velocity and safety.
