The BSI report on the state of IT safety in Germany presents alarming figures: In 2023, the Federal Office for Information Security registered a median of 68 new vulnerabilities in software program merchandise daily, leading to nearly 25,000 new vulnerabilities per 12 months.
Security-related errors have been counted in packages of every kind, from specialist functions for business to server software program for corporations and smartphone apps.
Most of those vulnerabilities, round 47 p.c, enabled the execution of unauthorized instructions or program code. In this manner, the attackers may, for instance, set up ransomware on a pc, bypass safety measures, lengthen their very own entry rights, or learn out knowledge with a view to promote it to different teams or blackmail the homeowners.
Winrar executes embedded scripts and masses malicious code
In an earlier model of Winrar, attackers have been capable of smuggle scripts onto the consumer’s pc through a ready archive.
IDG
In August 2023, a safety vulnerability was discovered in the popular Winrar packing program that allowed felony hackers to execute scripts on the consumer’s pc. The trigger was an error within the instrument’s dealing with of file identify extensions.
On this foundation, it was doable to organize RAR archives in such a means {that a} script was robotically began when a file was opened and, for instance, further recordsdata have been downloaded from the web.
In August, Win.rar GmbH launched the revised model 6.23, which fastened the error. Version 6.24 is now obtainable. However, it’s probably that many customers are nonetheless working with an earlier, susceptible model of this system.
Another main downside is that many different producers have licensed Winrar’s compression mechanism and integrated it into their very own merchandise. One instance is the Total Commander file supervisor. Therefore, if a program gives to open and create RAR archives, it’s best to positively replace it to the newest model.
Further studying: The best antivirus for Windows

VLC Media Player is now obtainable in model 3.0.20, through which the vulnerability has been fastened.
IDG
The open supply software program VLC Media Player has been attracting media consideration for a number of years now, as safety vulnerabilities have been found again and again. However, a few of these have been false studies, similar to a information merchandise from 2019.
The error solely affected the Linux model of the VLC participant and, in line with the VLC builders, the trigger was not of their software program however in a defective program library in some Linux distributions.
However, it has been confirmed that some VLC downloads from unofficial websites comprise a international DLL file that’s loaded when the instrument is named up and subsequently permits entry to the pc from outdoors. The lesson realized: Only ever obtain software program from the producer’s web site or from reliable websites.
In 2022, nevertheless, numerous vital safety vulnerabilities in VLC Player additionally turned identified. These made it doable for an attacker to trigger the instrument to crash through a ready file, for instance, and retrieve malicious code from exterior sources or set off a denial of service, i.e. paralyze the pc. All the consumer needed to do was play a video file or open a playlist.
The producer Videolan fastened the issues with model 3.0.18; the present model is 3.0.20.
Images within the graphic format Webp deliver malicious code with them
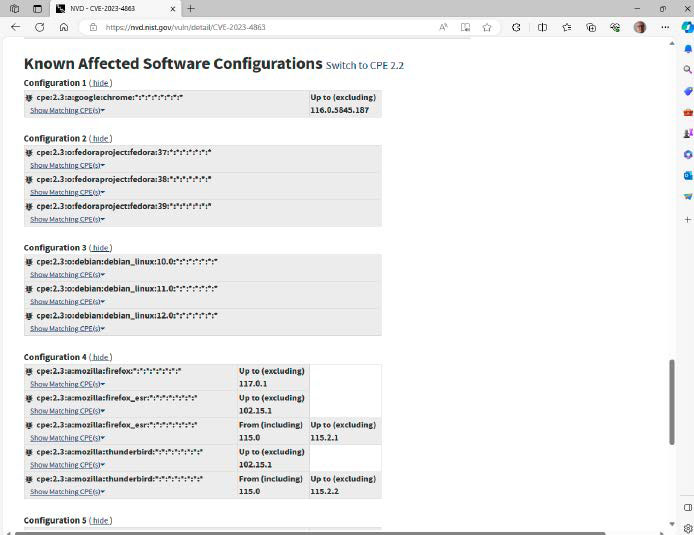
In addition to Google Chrome, the entry within the NIST vulnerability database lists a number of different packages and working techniques that have been susceptible to the flaw within the Webp graphics format.
IDG
Last September, Google registered a vulnerability in its Chrome browser that allowed attackers to set off a buffer overflow and execute malicious code. The extensively used graphic format Webp, which is characterised by notably small file sizes, was affected.
All a consumer needed to do was open a crafted picture on this format and the code was executed on their pc. With Google Chrome, it was adequate to open an internet site with a Webp picture.
Just just a few hours later, the corporate corrected itself and defined that numerous different functions in addition to Chrome have been susceptible. In truth, the bug was not within the browser itself, however within the open library libwebp, which this system accesses when opening webp photos. This library can be utilized by quite a few different packages, together with Chrome, Firefox, and Edge in addition to functions similar to Gimp, Inkscape, Libreoffice, Signal, Thunderbird, and 1Password.
While patches have lengthy been obtainable for browsers, that are additionally put in robotically, many packages on customers’ PCs are most likely nonetheless working in outdated, unpatched variations. You ought to due to this fact instantly replace any software program that may learn Webp graphics to the newest model quantity.
How to guard your self from vulnerabilities in packages
Recently, quite a few severe safety vulnerabilities have been found in extensively used packages. These pose a large risk to PC safety. We will present you which of them vulnerabilities are concerned and how one can shut them.
- Install obtainable patches and new software program variations instantly. Use a instrument such because the free Ucheck to often test for brand new releases.
- Use a password supervisor similar to Dashlane or Bitwarden. Define a distinct password for every service, store, account, and so forth. and select lengthy and complicated character combos.
- Wherever doable, it’s best to use two-factor authentication.
- Regularly again up your most essential knowledge to an exterior medium, which you then disconnect out of your pc.
- Be conscious of the hazards of phishing mails. Check the sender’s tackle and the hyperlinks contained in messages from banks, streaming suppliers and supply providers particularly.
Memory errors in Foxit PDF Reader enable malicious code to run
A earlier model of Foxit PDF Reader had a vulnerability that allowed malicious code to be executed when opening ready PDF recordsdata. It just isn’t identified whether or not Foxit customers have been truly attacked.
IDG
In November 2023, several vulnerabilities were discovered in Foxit PDF Reader and Foxit PDF Editor that would result in reminiscence errors when opening manipulated doc recordsdata. It was then doable for an attacker to execute arbitrary malicious code on the pc.
The producer has now launched model 2023.3, which closes these vulnerabilities.
Further studying: The best password managers
Watch out: New Outlook model passes on login knowledge
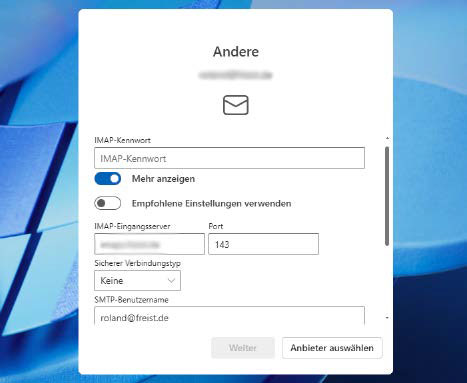
When organising the brand new Outlook, you’ll be requested in your IMAP entry knowledge, which is able to then be saved within the Microsoft cloud.
IDG
The days of the Windows packages Mail and Calendar are numbered. Microsoft needs to determine an e-mail program with a standardized interface and the identify Outlook throughout all working system platforms. The net model of Outlook is to be the mannequin.
The two Windows apps talked about above will even fall sufferer to those plans, and customers will probably be kind of gently urged to change to the brand new Outlook in Windows 11 within the coming months. It is already included within the present Windows 11. However, this isn’t the deliberate new Outlook model from Microsoft 365, which is able to solely be launched at a later date.
To make the change, customers must arrange their IMAP accounts within the new Outlook and likewise enter their consumer names and passwords. As has now been revealed, this knowledge doesn’t stay on the native pc, however is transferred to the Microsoft cloud and saved there.
Microsoft’s reasoning: this makes it doable to synchronize the entire consumer’s current e-mail accounts in order that they solely want one e-mail program for all of their mailboxes. However, if Microsoft has the entry knowledge, the corporate can learn all of an individual’s emails, each the messages in its personal providers similar to Outlook.com and the emails within the inboxes of different suppliers.
This article was translated from German to English and initially appeared on pcwelt.de.
