The web affords a wealthy choice of instruments for legal functions: password crackers and vulnerability scanners are simply two examples. At the identical time, one additionally finds net purposes which can be appropriate for violating privateness — for instance, reverse searches for the house owners of phone numbers or an individual in a photograph.
However, these instruments can’t solely be used for legal functions or to search out out the identification of different individuals, you too can use them in your personal safety or for emergencies. Password crackers, for instance, are sometimes the final resort when you have forgotten an vital password. Vulnerability scanners may also be used by yourself community to detect after which block potential entry factors for hackers.
Caution: Cracking passwords and even spying on networks is barely permitted by legislation if it entails your individual passwords and your individual community. If you attempt to decrypt another person’s password or spy on one other community, you’re liable to prosecution.
Replace Windows password
The Offline NT Password & Registry Editor can even overwrite Windows 10 and 11 passwords. An in depth information on the internet explains how to do that.
IDG
The first password it’s a must to enter after turning in your laptop is normally the Windows password. If you not know this password, your knowledge isn’t misplaced — you possibly can boot the pc with a boot stick or a boot CD, for instance, and replica vital paperwork to a different medium — however you normally don’t have any alternative however to reinstall the working system.
The free instrument Offline NT Password & Registry Editor affords a means out. It doesn’t even attempt to crack the password, however merely overwrites it with a personality mixture of your alternative.
The instrument is already fairly previous, the final model dates from 2014, nevertheless it nonetheless runs below Windows 10 and 11, albeit with some restrictions. For instance, the pc should assist legacy mode when booting; this system doesn’t work with a UEFI boot. In addition, the exhausting disk or SSD should not be encrypted with Bitlocker or another software program.
Also notice that Windows’ built-in encryption, the EFS file system, is tied to the password. If you alter it with the Offline NT Password & Registry Editor and had beforehand encrypted your exhausting drive, the info might be misplaced.
A information on how one can use the Offline NT Password & Registry Editor can be found here.
Passwords of Office paperwork
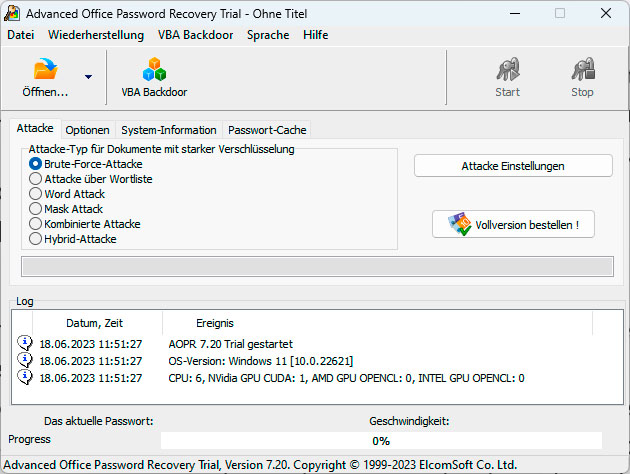
The instrument Advanced Office Password Recovery from Elcomsoft is aware of a number of strategies to crack the password of a locked Office file. In the free model, it finds passwords with a most of three letters.
IDG
Microsoft 365 packages reminiscent of Word, Excel, PowerPoint, and so forth. can password defend and encrypt paperwork. Microsoft has strengthened this encryption considerably with every new model.
You can subsequently discover a complete vary of instruments on the web that may crack the passwords of older Office variations, however that is hardly potential with the newer builds of Microsoft 365.
One exception is Elcomsoft Advanced Office Password Recovery, which may decrypt paperwork from all Microsoft Office variations. According to the producer, the software program can even decide the passwords of Wordperfect Office, Openoffice.org, and several other different Office packages.
To be sure that the method doesn’t take too lengthy, the software program makes use of a number of GPUs. The instrument is accessible for a payment, the house model prices $49. The producer affords a check model without cost obtain, which, nevertheless, solely shows passwords with a size of as much as three characters, which is able to hardly be adequate in any case.
PDF paperwork that you’ve got password-protected through Adobe Acrobat or Word are a particular case. For them, you want a separate program, particularly Elcomsoft Advanced PDF Password Recovery for $49 as nicely. A restricted check model can be obtainable for this instrument.
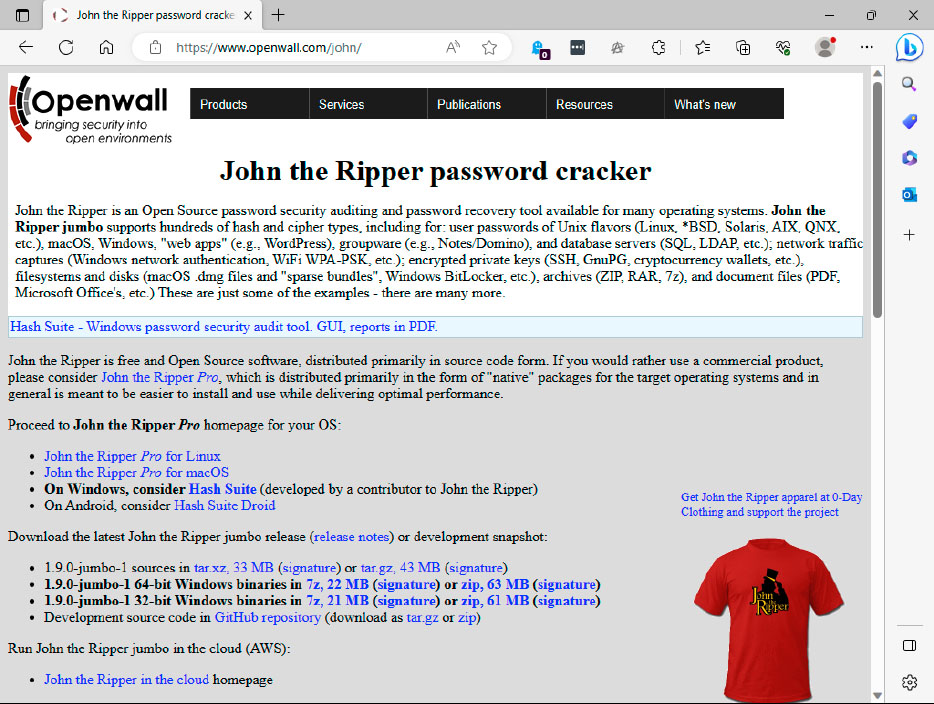
John the Ripper is an open-source program that cracks passwords from varied Office codecs and different packages because of a number of extensions. However, this could take a number of hours and even days.
IDG
The different to Elcomsoft is the free command-line program John the Ripper. You management the software program through the command line, so the operation is a bit more sophisticated. With the assistance of extensions, nevertheless, you should utilize the instrument for decrypting Microsoft 365 recordsdata in addition to for Libre Office or encrypted ZIP recordsdata.
Try out how lengthy the Elcomsoft packages and John the Ripper take to find out a password you’ve gotten used. This gives you an concept of how safe your password actually is. Keep in thoughts that legal hackers might have entry to present high-performance computer systems with a number of GPUs and correspondingly excessive computing energy. Their efficiency can exceed that of a PC by an element of 100 or extra, a minimum of in relation to such particular duties.
Scan your individual community
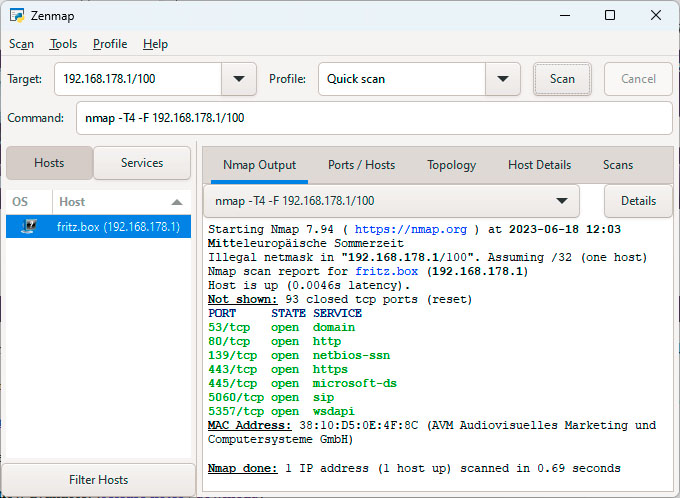
Nmap was initially a Linux instrument for the command line. In the meantime, a Windows model with a graphical person interface can be obtainable, which makes it a lot simpler to make use of.
IDG
If malware manages to get onto your laptop, it can typically attempt to infect different computer systems in your community as nicely. As a safety measure, you possibly can topic the gadgets in your community to a vulnerability evaluation. The best-known instrument for that is the open-source software program Nmap.
It seems to be for open ports by means of which the gadget could possibly be accessed from the surface and infers the working system, its model, the working providers, and the put in firewall from the port configuration and different knowledge. If vulnerabilities are identified for a discovered configuration, a legal hacker can exploit them and take over the pc.
Nmap is an expert instrument and requires some information about how networks work. At https://nmap.org/docs.html yow will discover detailed directions for this system, each for the command line model and for the model with the Windows interface. Research could also be required to interpret the info offered by Nmap.
Testing the Wi-Fi password
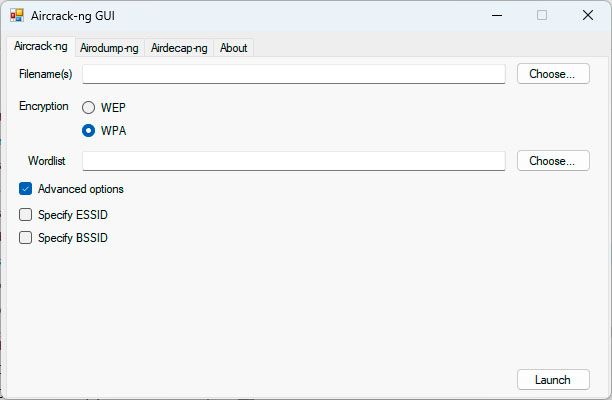
The graphical person interface of Aircrack-ng may be very sparse. Nevertheless, this system is difficult to make use of and likewise requires particular {hardware} parts to have the ability to pull knowledge in any respect.
IDG
The safety of a Wi-Fi community relies upon largely on the password used. For this cause, Wi-Fi passwords are sometimes very lengthy and sophisticated. To crack Wi-Fi encryption, it’s also essential to document and analyze the info visitors between the entry level and a shopper for a very long time. Alternatively, perform a brute power assault and take a look at character mixtures till you give you the password for the community entry.
The instrument Aircrack-ng goes one other means: It searches for the pre-shared key, a key that’s exchanged between the entry level and the shopper laptop for the encryption of the info. Possible areas are the recorded knowledge visitors within the type of a file or a monitored Wi-Fi community.
Aircrack-ng solely works with quite a lot of chosen Wi-Fi chipsets and antennas. It can be not straightforward to function. In addition, it will probably realistically solely decrypt shorter passwords. Decrypting the 20-digit password of a Fritzbox, for instance, is hopeless.
For a safety check, nevertheless, this function is good: If Aircrack-ng can crack your Wi-Fi password, it’s too brief.
Hiding your identification on the web
The Tor community remains to be your best option for transferring across the web undetected. It is true that registration through Tor can be a prerequisite for visiting the Dark Web, the place unlawful items are traded on many websites.
But Tor can be the most secure means for many individuals in repressive states to entry web sites undetected that aren’t accessible in their very own nation. Here within the United States, TOR is just a safe option to stay nameless on the web. You can even ship emails or use social media through the community — Facebook has been working its personal web site on the Dark Web for a number of years.
To entry Tor, all you want is the free Tor browser, a custom-made and pre-configured model of Firefox.
If you wish to be on the protected facet, use a reside CD with the Linux distribution Tails, which additionally permits entry to the Tor community, and boot your PC with it.
Reverse search: images
Pimeyes is a search engine particularly for faces. You can add a portrait to the web site or snap a photograph along with your smartphone, and the online service will search its database for extra footage of the identical particular person in a cut up second. It then presents you with the images it has discovered and names the web sites the place it discovered them.
Three searches are free, however the service doesn’t identify the corresponding net addresses. You need to pay $14.99 per search to activate them. For additional searches, you are taking out a subscription, which prices $29.99 per 30 days within the most cost-effective model.
Google additionally affords an analogous service freed from cost. The search engine affords a picture search at www.google.com/imghp. If you click on on the digicam image to the proper of the search area, you possibly can add a photograph. After clicking on “Search,” modify the picture part after which click on on “Search image source.” Google will then current you with a listing of which web sites this picture seems on.
There is one distinction between the 2 providers: Pimeyes is ready to seek for footage of the identical particular person, so you possibly can establish them by a caption, for instance. So it’s a service for face recognition. Google’s picture search, then again, solely finds the identical or comparable images on the internet. However, each engines like google can be utilized usefully to seek for unauthorized use of copyrighted photographs, for instance.
This article was translated from German to English and initially appeared on pcwelt.de.
