The conveniences of recent life additionally include downsides. One downside that may have an outsized impression on an individual is digital stalking—using your digital footprint to maintain tabs on you on-line and in the actual world.
But you’ll be able to take steps to attenuate that danger. You don’t have to go to excessive lengths to take care of your privateness, both. Basic precautions will set you up properly for the long run, like turning off public sharing for social-media posts.
But you’ll be able to go even additional to extend your safety measures to stop cyberstalking—and most of the people involved about digital stalkers will wish to accomplish that. Vulnerabilities can overlap. For instance, social media can reveal details that may make stalking you digitally and bodily simpler. And having the identical consumer identify throughout all apps and providers might make discovering you on the net and discovering one in every of your long-forgotten accounts with a weak password a lot less complicated. (Both can result in additional intrusion into your life.)
This article breaks every little thing down for you, with bolded textual content that highlights key motion objects. Use it as a guidelines to shore up your defenses.
Quick privateness ideas
As you learn by means of this text, you should use an incognito or non-public shopping window (right-click on these hyperlinks and select “Open link in incognito window” or “Open in private window”) when you really feel that your pc won’t be safe from an in-home risk.
Also, digital stalking can result in real-world hazard. If you consider you’re in danger, don’t cease after implementing the following pointers. Resources for people experiencing stalking, domestic abuse, and other violence exist, and you may seek the advice of with them and native teams (in addition to native legislation enforcement or your nationwide police power, e.g., the FBI) to get additional assist. And maintain a paper path when you consider somebody is stalking and/or threatening you. Write down incidents of concern and take screenshots (or video) as a lot as doable.
Ways folks can monitor your on-line exercise
Your profile is about public
PCWorld
Your social media accounts or different apps and providers could also be broadcasting all your posts or info for anybody to view. Remove the data or set your privateness degree to friends-only (at minimal) to maintain these deets away from prying eyes. Unfortunately, you’ll be able to’t all the time predict which corporations will do that, so you will have to comb by means of a variety of apps and web sites for an intensive lockdown.
Also, if you’re tagged or in any other case named in different folks’s public posts, somebody can see into your life. You can change your settings to dam others’ potential to tag you.
Your consumer identify
Many folks use the identical consumer ID throughout all providers. To keep away from somebody following you across the web, combine it up. Use a singular login identify for some providers, if not all of them. If you employ a password manager, you’ll be capable of simply maintain observe of your consumer IDs.
Through your folks
Not solely can different folks’s public posts disclose specifics about your life, however your “friends” on web sites or apps may develop into a vulnerability. You gained’t all the time know who they know, and what finally ends up getting shared not directly.
You can reduce this danger by limiting your posts’ attain to trusted people, eradicating folks you don’t know properly from your folks listing, and/or just not sharing as a lot on-line.
Account infiltration

Soumil Kumar / Pexels
Another individual can entry your account when you’ve got a weak, leaked, or shared password, or by means of any linked third-party providers which have been compromised. Let’s say that you just use Facebook to log into different web sites. If somebody positive factors entry to your Facebook account, that might open up entry to a ton of different websites as properly.
At its most benign, you would possibly end up with a freeloader in your Netflix account. But even in that case, that individual can nonetheless see your viewing habits and a few of your billing particulars, in addition to your e-mail handle and probably telephone quantity, too. Such knowledge can permit deeper digging into your life and snooping on private messages or e-mail in case your safety is weak general. Your monetary info, intimate conversations, and personal images might find yourself uncovered.
To root out a spy, examine your account exercise. Many main providers (Gmail, Facebook, and many others.) present an inventory of IP addresses and the units related to them, in addition to the time and date of the entry. You can determine your IP handle by typing “what’s my ip” into Google or one other search engine. (Your telephone could have a distinct IP handle than your PC when you use its mobile knowledge connection.)
If you see any unknown IP addresses, log off that machine or finish its session. Also change your password as properly to one thing robust and random. A password supervisor (even a good free one) will make that straightforward. Enable two-factor authentication to lift your safety degree even additional, and restrict third-party entry to your accounts. Even when you don’t see any suspicious exercise, you’ll be able to nonetheless undergo these steps to make sure you (and solely you) have account entry.
Physical entry to your machine(s)
Incognito home windows in Chrome are a strategy to maintain folks with entry to your machine from realizing your shopping historical past. The identical mode exists in different browsers too however are named in a different way.
PCWorld
Checking IP addresses in your account exercise will let you know when folks outdoors your own home are monitoring you, however not essentially when somebody inside your own home is doing the watching. You would possibly catch them that manner on their very own units, however not after they use yours.
Maybe you don’t have a display lock in your telephone or an account password in your PC. Or maybe you’ve shared that information prior to now with a housemate, buddy, or member of the family and by no means modified it. They can then take a look at any web site or app you’re logged into. No want for the passwords to these accounts.
Keep folks out by including an authentication methodology to the machine—or altering your present credentials. If that’s not an possibility, log off of internet sites and purposes if you’re not utilizing them. For net shopping, you too can use an incognito window in Chrome, InNon-public window in Edge, or a personal window in Firefox to keep away from leaving a historical past of what websites you go to.
A non-public shopping session gained’t stop somebody on your own home community from with the ability to see your site visitors requests, although. To cowl that utterly, you’ll want to make use of a VPN. Alternatively, you should use your telephone’s mobile knowledge connection.
Remote entry to your PC
TeamViewer is a well-liked app that grants distant management of your pc to another person.
TeamViewer
Checking account exercise logs additionally gained’t reveal if somebody is monitoring you through distant entry to your PC. It not solely permits them to see every little thing you do in actual time, but additionally management your pc.
If somebody doesn’t have bodily entry to your units, you’ll normally need to click on a malicious hyperlink for them to achieve distant entry. So don’t click on on any hyperlinks you don’t acknowledge. Also run common, thorough antivirus and antimalware scans on your PC. If you employ Chrome, examine your Chrome Remote Desktop settings as properly to ensure nobody has unauthorized entry your PC. (And make sure that the Google account you employ to signal into Chrome is safe.)
Someone with bodily entry to your units could surreptitiously arrange distant entry software program with out your data. One straightforward manner to do that is popping on Remote Desktop, a function constructed into Windows 10 Pro and Windows 11 Pro, or Apple Remote Desktop, the equal for macOS. Go into your settings to revoke entry to unrecognized accounts or flip off the function utterly.
Third-party software program options for Remote Desktop and Apple Remote Desktop additionally exist. You can search for these by scanning by means of the put in apps in your PC. In Windows, sort “Apps & features” into the Start menu or search bar, then begin trying on the listing of apps. On a Mac, open the Applications Folder. (Check each the one tied to the system, and the one tied to your consumer account.) Obvious remote-access software program contains TeamViewer, however you’ll be able to Google the identify of any program you don’t acknowledge. Uninstall any monitoring apps that don’t belong in your system.
Ways folks can monitor your bodily location
You can leak info in your present bodily location and even common haunts by means of what you share on-line, both knowingly or not. Here’s the right way to plug that.
Social media
PCWorld
Public posts on Facebook, Twitter, and Instagram that tag or point out a location are a useless giveaway of the place you’re at or the place you want to go to. You may give away your locale by means of sharing images with landmarks or particulars recognizable to whomever is viewing the photograph.
To resolve this drawback, lock down your posts. You could make your account non-public on Instagram and Twitter, and on Facebook, you’ll be able to select to restrict who you share posts with. Make them Friends-only at minimal, or much more restricted when you’re linked to folks you don’t know properly. (You don’t know who they know, a lot much less who could attempt to use them to get to you.)
Alternatively, you’ll be able to simply cease tagging or mentioning the place you’re at. If you should, wait till after you’ve departed—and restrict the behavior to locations you’re solely visiting as soon as, slightly than spots you frequent. You may change your settings to dam others from tagging you in images or places by default.
Also be conscious of what you share. You’re not required to reveal your own home handle, office, schooling, or different figuring out particulars. (You could have to share a telephone quantity for two-factor authentication, however you should use a Google Voice number that may’t be simply traced to you.) Only reveal info when completely needed and maintain it as common as doable.
PCWorld
Photos
Photos shared on-line can betray your location in two methods. You have geotagging enabled for images you’re taking in your telephone, otherwise you’ve taken a photograph with sufficient background particulars to disclose the place you might be. (Or each.)
You can both flip off geotagging fully in your images, or earlier than posting a photograph, run it by means of an app that strips its metadata (together with location and the machine used to take the snap). If you solely have to take away location knowledge, strive Adobe Photoshop Express on Android; on iOS, strive Snapseed. (Don’t reverse these suggestions, although the apps exist for each platforms.) You’ll open your present file, then save/export it. In your Photos app, you’ll be able to take a look at the data of the copied photograph to confirm that the GPS knowledge is gone.
As for what you’re taking photographs of, be conscious of what’s within the background behind you earlier than you put up a photograph. You could not be capable of get rid of all clues to the place you might be, although, so being cautious about whom you share the photograph with can be a technique.
Other apps and providers
Similar to social media, your settings in some apps and providers can broadcast your common haunts or habits. For instance: Fitness apps that observe your route when working or biking could make that public info by default. A journey app that blasts your itinerary to the huge web. A calendar that’s set to public. Websites that permit anybody to see your want lists and favorites.
Even Venmo can reveal the individuals who you work together with most, when you go away your transactions public—and if their settings are much less lax than yours, it may well once more spill perception into your life you’d slightly maintain non-public.
Take the time to undergo the settings of your apps and providers. Verify that your particulars aren’t public at minimal, and contemplate locking down any extraneous info. Share solely the minimal with pals as needed (e.g., they most likely don’t have to know your actual run route for health challenges, solely that you just did eight miles). To actually go non-public, don’t neglect outdated accounts you employ hardly ever or have deserted.
Public document

Ethan Hoover / Unsplash
Your dwelling handle is less complicated to search out than you would possibly suppose. Past ones, too. At least, that’s true within the United States—even when you’ve by no means filed a change of handle kind with the U.S. Postal Service or purchased a home, companies you patronize could have shared your information with knowledge brokers. That contains banks and different extremely private providers.
Restricting this information can take a bit of elbow grease, however it’s doable. First, carry out a search on Google and different serps in your identify to see what sort of particulars instantly turns up. (You might have so as to add your location when you’ve got a standard identify.) If you see any people-search websites come up (like whitepages.com, spokeo.com, and many others.), search for your itemizing. If you discover one, you’ll be able to use the location’s opt-out course of to get it eliminated.
Unfortunately, many people-search websites exist, and it may be a little bit of a sport of whack-a-mole attempting to maintain your self off them. To cut back such work sooner or later, choose out of information sharing throughout the entire providers you employ, together with monetary establishments like banks. You usually can simply name and speak to customer support to have this completed. California residents ought to get a yearly discover that lets you change your data-sharing preferences.
Domain registration
Do you might have an internet site with your individual area? If your area registrar doesn’t provide non-public registration (otherwise you didn’t activate the function), your identify, handle, telephone quantity, and e-mail handle might be discovered by anybody.
The repair is straightforward. If your registrar provides non-public registration, flip it on. Your registrar will substitute their very own contact information for yours, and ahead you any incoming messages from folks attempting to get in contact about your area.
If your registrar doesn’t provide non-public registration, transfer to at least one that does. We have a curated list of the best domain registrars that you could reference.
Apple AirTags (and different Bluetooth trackers)

IDG
A Bluetooth tracker is a small bodily object that may be positioned on objects to make sure they don’t go misplaced. That’s their intent, not less than—however they can be utilized for stalking, too. Because the individual would want to have entry to your automobile, bike, bag, or different belonging, this type of monitoring your actions depends on not less than an preliminary second of shut proximity.
Apple AirTags are probably the most probably harmful of the Bluetooth trackers, because of what number of Apple units can be found for a tracker to ping off of and thus set up your location and route of motion. But Tile, Chipolo, and different trackers work similarly.
Our sister website Macworld has a full rundown of Apple’s steps to thwart stalking, in addition to a information on how to avoid being tracked via an AirTag. It explains in additional element the right way to use Apple’s built-in apps and instruments to scan for trackers in your neighborhood (even when you’ve got an Android machine). Tile additionally provides the power to scan for unknown trackers, however not all different distributors do.
Unfortunately, you should have a smartphone or pill in an effort to carry out this sort of scan. Otherwise, you need to hope that you could hear an Apple AirTag’s beeping, which signifies a “lost” tag. Other Bluetooth trackers sadly should not have this function.
If you might have purpose to consider somebody would possibly place a tracker on you, in your stuff, or in your automobile, it’s possible you’ll wish to start often checking your stuff for something that doesn’t belong.
Phone location
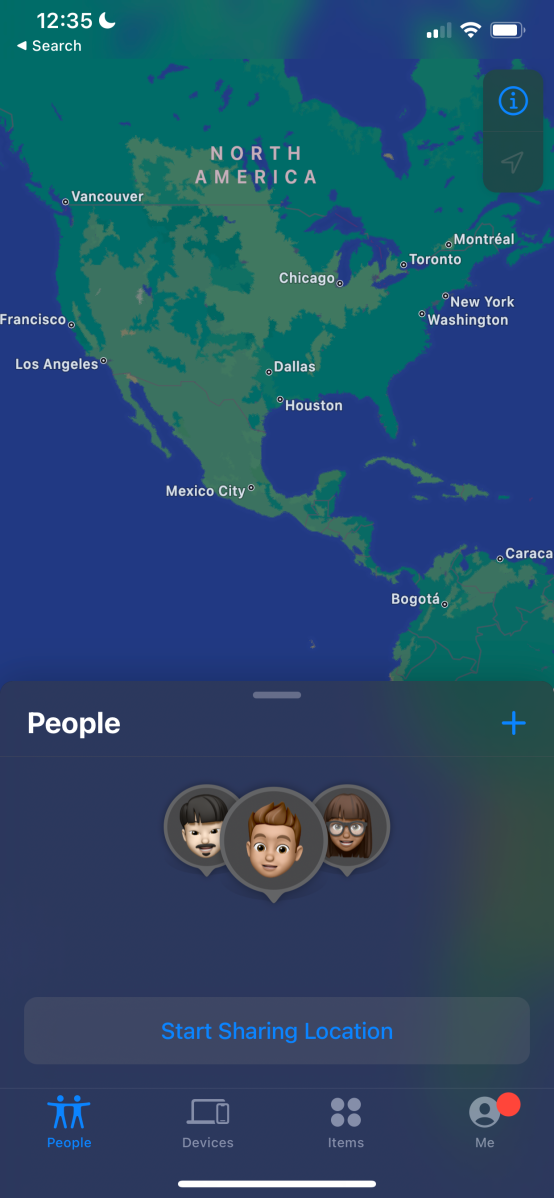
PCWorld
Your telephone could also be betraying your location to your family and friends—or anybody deemed as such in your settings.
If you might have location settings on (this permits your cellphone to share your GPS location with apps, which is important when utilizing a map app, experience sharing, or permitting an app to examine into a spot), it’s doable for choose contacts to trace you in actual time when you permit it. In idea, solely it is best to have management over this, but when somebody has had bodily entry to your telephone, they’ll grant permission to themselves or others too.
It’s a sword that cuts two methods: Useful if you could maintain observe of your ageing relative who typically will get misplaced going dwelling on public transit, however harmful if it’s an individual who shouldn’t have that information.
On iPhone, you’ll be able to examine to see who has this degree of entry in your Find My app. On Android, sharing is completed by means of Google Maps—click on in your profile icon, then go to Settings > Location Sharing.
