LastPass is without doubt one of the greatest third-party password managers on the market and it used to carry that place for an excellent purpose. The free plan supported a number of varieties of units, the paid plan was a worthwhile improve for $12 per 12 months, and it had a good sufficient consumer interface total. Even when the corporate suffered from a number of safety incidents, its responses appeared to warrant the advantage of the doubt.
But over time, options obtained lower from the free plan and the value of the paid plan went up. Rival password managers additionally began pushing extra revolutionary options. And then got here the foremost breach in 2022, one wherein knowledge in prospects’ vaults have been stolen and revealed as not totally encrypted.
A protracted whereas again, I began an account with LastPass to keep up the passwords for a cherished one and even after final 12 months’s hack, I didn’t depart instantly. (Change is tough for this particular person). But after some light, extended coaxing, I obtained the inexperienced mild to modify them to a different password supervisor eventually and I’m so glad to lastly transfer on to greener pastures. LastPass’s issues are simply too quite a few to stay it out…together with if you’re truly within the strategy of leaving.
If you’re nonetheless with LastPass and been questioning when you ought to soar, right here’s what tipped me over the sting and why I don’t plan on ever returning.
If you’re trying to decide up a password supervisor, you need to take a look at PCWorld’s roundup of the best ones available today.
The 2022 safety breaches
PCWorld
LastPass’s disclosures about its 2022 safety breaches was like watching a prepare wreck in sluggish movement. First got here the initial announcement in August, which claimed that no buyer knowledge was affected—only a developer surroundings. Then three months later got here an replace that buyer knowledge was affected. Nearly a month after that, the corporate revealed that buyer data and password vaults had been stolen. Not solely that, however components in these vaults (together with URLs) had not been encrypted.
As talked about above, LastPass was no stranger to safety incidents earlier than this breach, however none have been as surprising as this one. Customers of on-line password managers typically belief that their service is safeguarded sufficient that their knowledge—even when encrypted—can’t be accessed by unauthorized events. Hearing after a breach that vault knowledge was unencrypted was a bit blindsiding.
And maybe there’s good purpose from an engineering perspective for why some particulars—like URLs, how typically you employ an entry, if you final up to date an entry, and so on—wouldn’t be encrypted. But that brings us to the second means LastPass skewered my belief in them, which is…
Bad communication
PCWorld
So, clearly, I don’t know what it takes to run a enterprise the place you’re not solely safeguarding actually delicate data, however you’re actively coping with threats to that data regularly.
But good communication is fairly primary, immediacy and full transparency go a great distance. A wholesome dose of preemptive notifications works wonders, too. The means LastPass breaks its information to prospects may use numerous enchancment on all three fronts.
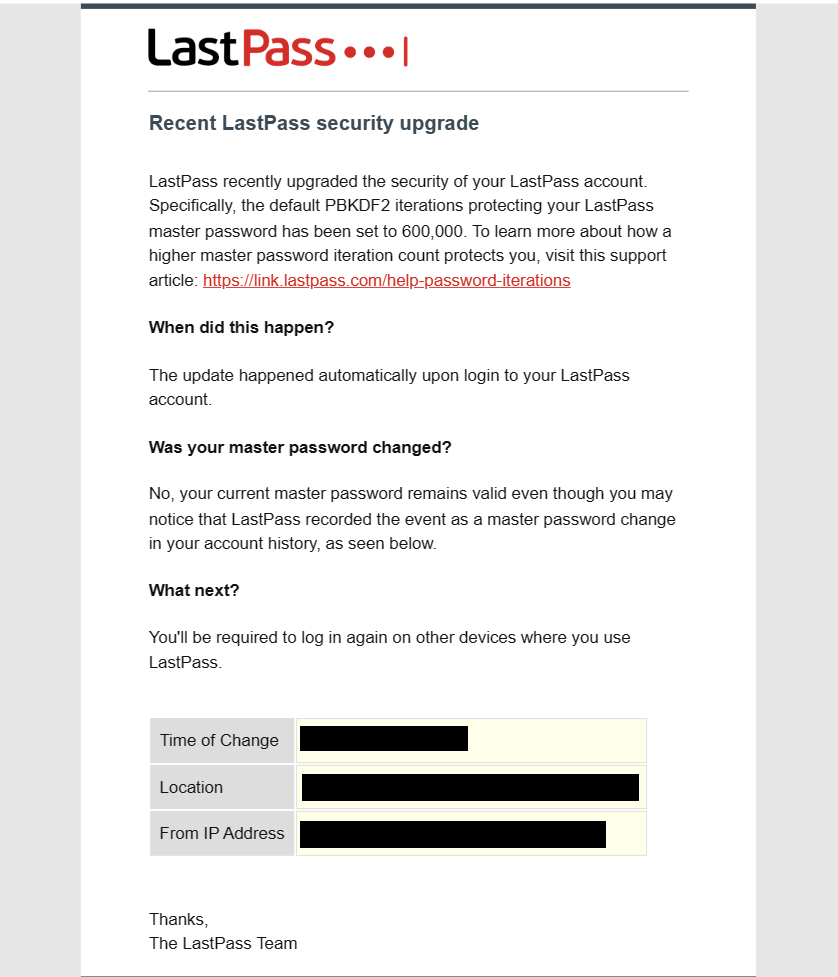
Let’s take a latest instance. In mid-July, I logged in to make a final test of the account I used to be abandoning, solely to see a message that my password iterations had been raised to 600,000.
The next variety of password iterations is in idea an excellent factor. It’s supposed to assist decelerate the power to rapidly guess what your password is. Modern cryptography requirements recommends 600,000 iterations, which might be why LastPass selected to spice up prospects universally to that degree.
But this occurred in July 2023. That is, six months after the disclosure in December about everybody’s vault knowledge being stolen. A half 12 months handed wherein individuals who didn’t test that setting again in December (like I did) and elevated it (like I additionally did) have been left with a lot decrease iterations (like mine was earlier than I fiddled with it).
It says lots that my first thought was, “What sort of safety difficulty did they’ve this time to immediate this?” Also, that my second one was, “Why is that this occurring now?”
The e mail explaining this modification got here a number of hours after I made a fast on-line search to determine simply what the heck was occurring. Then one other copy got here within the subsequent day. The contents didn’t clarify the timing nor the motivating purpose behind the rise.
The internet interface is disappointing

PCWorld
Once upon a time, LastPass’s internet interface was fairly first rate. Maybe not the slickest, nevertheless it felt trendy sufficient.
Nowadays, it feels way more bare-bones in comparison with rival password managers. Small adjustments over time has degraded the online interface, too. My greatest beef is that it depends closely on persistent cookies to keep up settings. Incognito looking signifies that your structure won’t ever stay saved—it at all times reverts the view to LastPass’s default.
Banner messages seem repeatedly, too. Perhaps that is petty of me, however when a everlasting banner message appeared for the browser extension appeared, that was once I lastly reached my restrict. LastPass has the logs of what units I’ve used and my constant, unrelenting use of the online interface for years and years. Being nagged persistently just isn’t going to make me change that behavior.
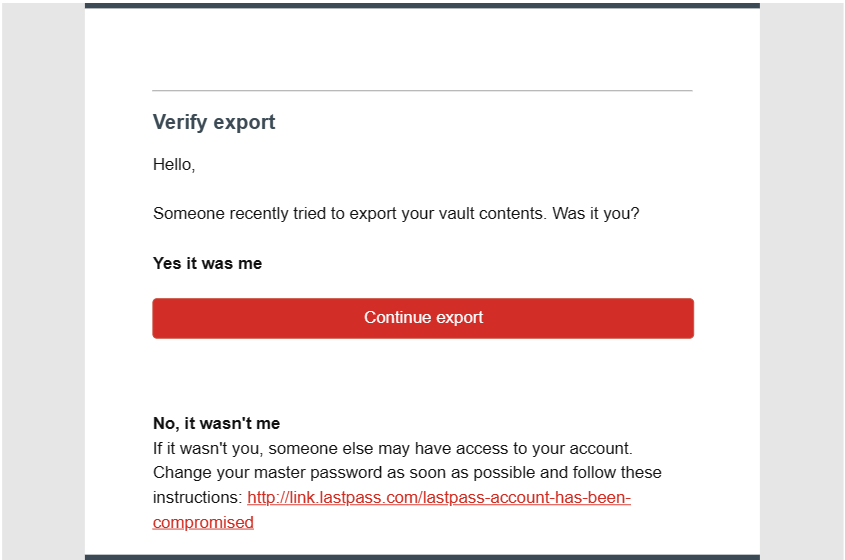
Exporting your vault is a nightmare
PCWorld
This part was full of far saltier language till I remembered you all (and my editor) can be studying it. Roll up your sleeves, as a result of we’re moving into the soiled particulars with this one.
You’d assume that maybe, when you have been leaving a service, the enterprise can be incentivized to make the method as simple as attainable—thereby growing the probabilities you may return sometime. LastPass tries for this, nevertheless it doesn’t do it persistently. And fortunate me, I obtained caught up in no matter growth gap that permits for sloppy password exports.
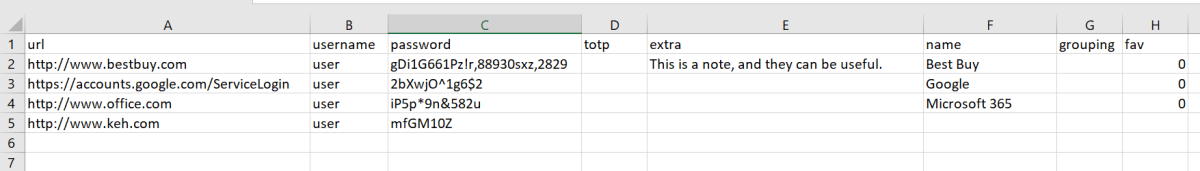
Generally, if you swap password managers, you’ll export your vault knowledge to a CSV or XML file. They’re primary file codecs that may be simply learn throughout totally different packages (in idea, anyway). LastPass solely exports to CSV for this objective and the defining attribute of the comma separated values format is that (as you’d count on from the identify), commas are used to point separate knowledge fields.
Note: If exporting all of your passwords to an unencrypted format like CSV or XML, saving it to an encrypted folder on your PC will assist safeguard them as you transition between LastPass and a brand new password supervisor.
I need to be clear—I’m the sort of individual that if one thing goes wonky, I like to know why. And when my export got here out a large number, with a bunch of entries containing orphaned knowledge, I attempted to make sense of what I used to be seeing.
At first, I believed the basis trigger was commas within the textual content fields. That maybe they have been inflicting entries to be cut up up and browse as totally different entries (with knowledge ending within the unsuitable fields, as well). But that didn’t clarify why some entries with no commas in any respect obtained cut up up. Or why different entries have been simply plain lacking.
PCWorld
I nonetheless had no clear solutions by the point I completed manually cross-checking each single entry towards the originals in LastPass, a crucial evil as a result of the info was untrustworthy, however importing and cleansing up the mess was nonetheless quicker than creating all of the entries from scratch within the new password supervisor.
Trying totally different browsers and strategies of export (i.e., initiated by way of the online interface vs the browser extension) didn’t clear up the confusion. Turns out the online interface doesn’t export all entries (Firefox) or straight up returns a clean CSV file (Chrome), however each Firefox’s internet interface export and the Chrome browser extension had the identical points with knowledge integrity. Meanwhile, once I tried exporting on a check account, the info fields for every entry got here out good (even when some have been nonetheless lacking within the internet export).
As greatest as I can inform, both the age of the account influences how the info is saved and parsed on the servers, or the usage of sure particular characters in non-password textual content fields triggers some sort of bug within the export script. Either means, you’ll be able to’t belief you’re truly getting all of your passwords out intact. Hours into the tedious strategy of salvaging my import, I critically thought of abandoning the method in favor of password resets for each service, and letting the brand new password supervisor seize them. I imply, I used to be going to have to try this anyway as a ultimate precaution given the LastPass safety breaches, proper?
Never once more.
If you’re trying to decide up a password supervisor, you need to take a look at PCWorld’s roundup of the best ones available today.
