Antivirus software program isn’t freed from errors and typically reviews laptop viruses the place there are none. For this motive, the corporate Procolored, a producer of textile printers, indignantly defended itself in opposition to the report of a printer tester that the software of one of its devices contained a virus.
The testing official defined to Procolored that each Google Chrome and Microsoft Defender had triggered an alarm when the printer software program was downloaded, and quarantined it.
Despite Procolored’s protests, the tester endured. He despatched the software program to the safety firm G Data, a producer of antivirus packages.
Upon investigation, it turned out that the printer software program truly contained a backdoor virus referred to as Xred and a Trojan.
When G Data then confronted Procolored with the outcomes, the corporate admitted {that a} virus had crept into its obtain space and supplied a brand new model of its software program.
The on-line sandbox Any.run enables you to begin suspicious packages in a digital Windows atmosphere and examine their habits.
Foundry
How false alarms come up
Procolored’s initially defensive angle is comprehensible. After all, it does occur that antivirus instruments typically acknowledge malware the place there may be none.
But not usually. Long-term assessments have repeatedly proven that false alarms normally account for lower than 1 p.c of virus reviews. However, they’re at all times annoying, as many customers are initially alarmed when their laptop reviews malware.
How do these false positives come about?
It has to do with the best way antivirus packages work. On the one hand, they entry each day up to date virus definitions, which they will use to acknowledge intruders very reliably.
However, as there are additionally many beforehand unknown malware threats on the web for which no virus definitions exist, the producers additionally incorporate heuristic and behavioral evaluation strategies into their software program. Heuristic signifies that the packages search for suspicious traits of a file or program.
Behavioral evaluation, however, observes the packages working on the PC. Both strategies work with chances and calculate whether or not a program with these or these traits could possibly be a virus. False alarms happen once in a while.
System packages notably affected
False alarms happen notably often with packages that entry system settings or information that the antivirus program classifies as confidential and even secret.
This applies, for instance, to a number of instruments from the software program firm Nirsoft, such because the Produkey program. It reads the license keys for Windows and Office 2003/2007 and shows them in its window.
A innocent course of in itself, but it surely apparently offers the antivirus software program with sufficient suspicious information to categorise the applying as a virus.
The similar applies to quite a few different packages that learn out information similar to license keys or passwords or change system settings. Among different issues, the heuristics of the antivirus software program search for mixtures of sure system calls which might be typical of malware.
However, recognized hacker instruments, similar to these used to crack passwords, are additionally blocked by the virus guards. Even although they’re provided for obtain legally. Hacking your personal laptop, for instance to reconstruct a forgotten password, isn’t prohibited.
A superbly functioning antivirus program that produces no false alarms is an phantasm. On the one hand, the software program should not overlook malware beneath any circumstances, whereas however it ought to acknowledge innocent packages as such.
It is subsequently inevitable that the virus hunter will play it protected from case to case and report software program as harmful even when it isn’t.
Check the set off of a false alarm
If your virus safety triggers an alarm, you have to at all times scrutinize the set off your self. Otherwise, there’s a threat that the antivirus program will block elements of the software program which might be completely vital for it to perform. A multi-stage process is beneficial.
Check the aim of the software: As a primary step, you must take into account what you’ve downloaded. If it is among the instruments already talked about for figuring out license codes or passwords, you may assume that it’s a false alarm.
Check for popularity: However, you also needs to test the place you obtained the software program from and take into consideration its popularity. To do that, you have to have a look at the file that precipitated the alarm and make clear its origin.
If you might be utilizing Microsoft Defender as virus safety, yow will discover the file and its origin within the “Settings” beneath “Privacy and Security > Windows Security > Virus and Threat Protection > Protection History.”
All malware discovered by Defender is listed there. Click on one of many entries to search out out the file title and origin. There are related directories in each different antivirus program.
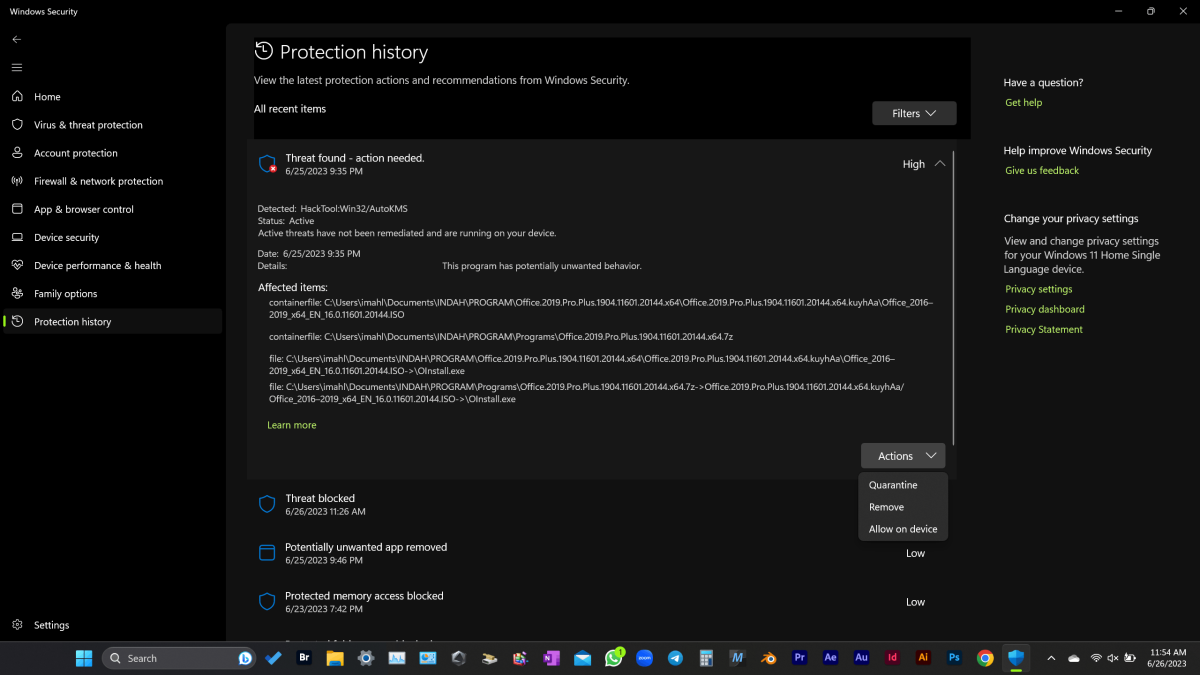
Defender lists probably the most lately discovered threats and reveals you particulars if you want. To do that, you have to level to an space with the mouse. A pop-down menu is then displayed.
Microsoft
It is vital to know the place you bought the file from and whether or not this obtain web site has a great or unhealthy popularity.
Sites that provide cracked packages and video games or instruments for hacking license queries and so forth., for instance, have a poor popularity. Hackers usually use this software program to switch malware to customers’ computer systems.
Websites that illegally make movies and movies out there for obtain additionally fall into this class.
Check for indicators of social engineering: Social engineering refers to methods that trigger an individual to exhibit sure behaviors that they might not exhibit with out these methods.
Social engineering is repeatedly used within the phishing of personal information and, considerably much less often, within the distribution of malware. For instance, emails or textual content messages declare that an order is at risk of getting caught within the publish if you happen to don’t take motion rapidly and set up a service software. However, that is truly a virus.
If the antivirus program now reviews malware, there’s a excessive likelihood that it truly is malware. Typical social engineering methods are stress, urgency, emergencies, and requests for assist.
Watch out for scams: On the web, the final rule is that if one thing appears too good to be true, then it normally is. This could possibly be very favorable buy presents, for instance. If a virus message seems in such a context, then it’s in all probability justified.
What to do within the occasion of a false alarm
If your antivirus software program declares a downloaded program to be malware, however you might be positive that it isn’t, you may outline the obtain file or the tackle of the supply on the web as an exception. Every safety program presents a corresponding perform.
Use different virus scanners
If your antivirus program has reported malware and you aren’t positive whether or not it’s truly malware or a false alarm, you may get hold of a second opinion from one other antivirus software in an extra step.
It isn’t essential to uninstall your current software program after which obtain and set up a competitor’s product. It is faster and simpler to scan the suspicious file with a web-based scanner.
Some antivirus producers provide on-line scanners as a free service on their web site. There is an space the place you may add suspicious information to the producer’s servers and have them scanned there.
Corresponding presents can be found from Eset, F-Secure, and Trend Micro.
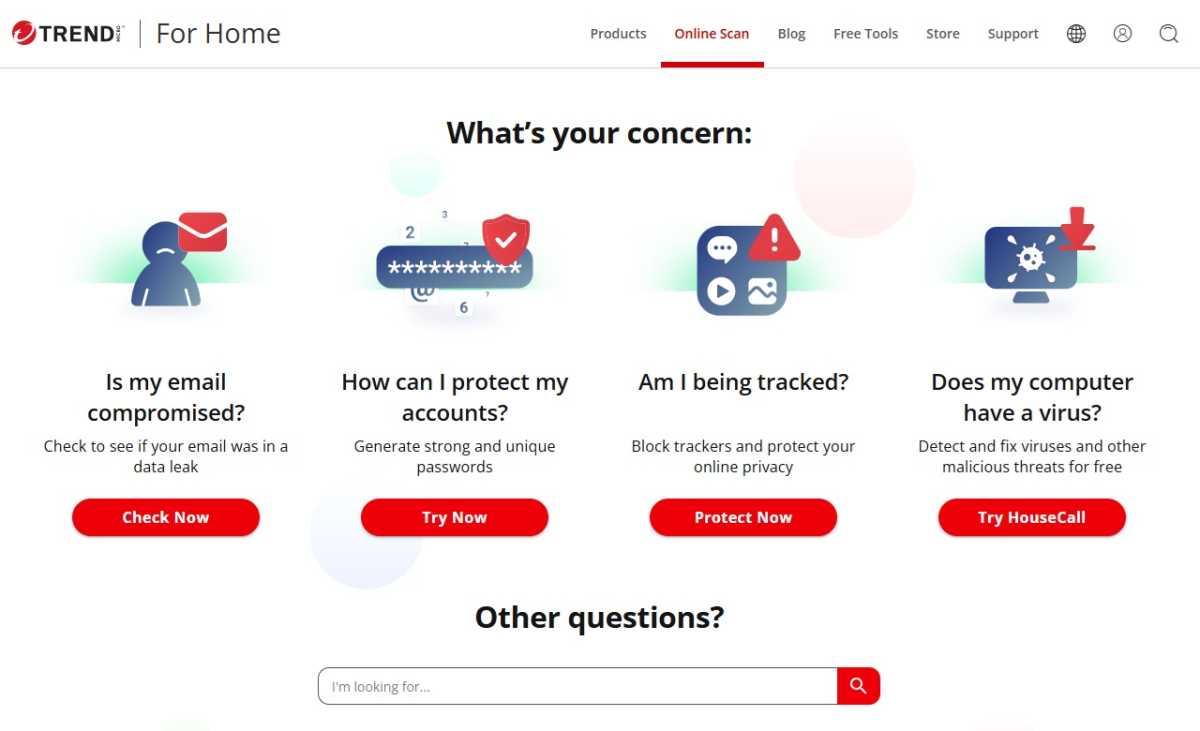
You can use the web scanner from Trend Micro to scan your laptop for current malware. No set up is required.
Foundry
Or you may go straight to Virustotal, the web scanner from Google. It presents the suspicious file to a number of dozen antivirus packages from numerous producers and shows their scan outcomes.
Although there have been remoted circumstances prior to now through which Virustotal additionally failed to acknowledge malware, that is in all probability the most secure technique to rule out a false alarm.
There are additionally alternate options to Virustotal, together with Metadefender Cloud, Hybrid Analysis, and Jotti’s Malware Scan.

Jotti’s Malware Scan is a substitute for Virustotal and sends uploaded information to a complete of 13 completely different antivirus scanners. There is an information restrict of 250MB per file.
Foundry
Offline scan with bootable USB sticks and DVDs
If you often use completely different computer systems, you may as well set up a virus scanner on a bootable USB stick or DVD. In this manner, you may test the respective PC first earlier than you begin your work.
There are a number of methods to acquire such a stick or DVD. Some antivirus packages comprise wizards that mean you can create a transportable model on a stick or DVD immediately from the software program.
This applies to the similar packages from Avast and AVG in addition to the paid-for Norton Antivirus.
The drawback: You should first set up the respective antivirus program so as to create the disc.
Other producers provide rescue discs as ready-to-use downloads. These discs are normally based mostly on a Linux stay system that has been supplemented with a virus scanner. They can be found from Avira and Kaspersky.
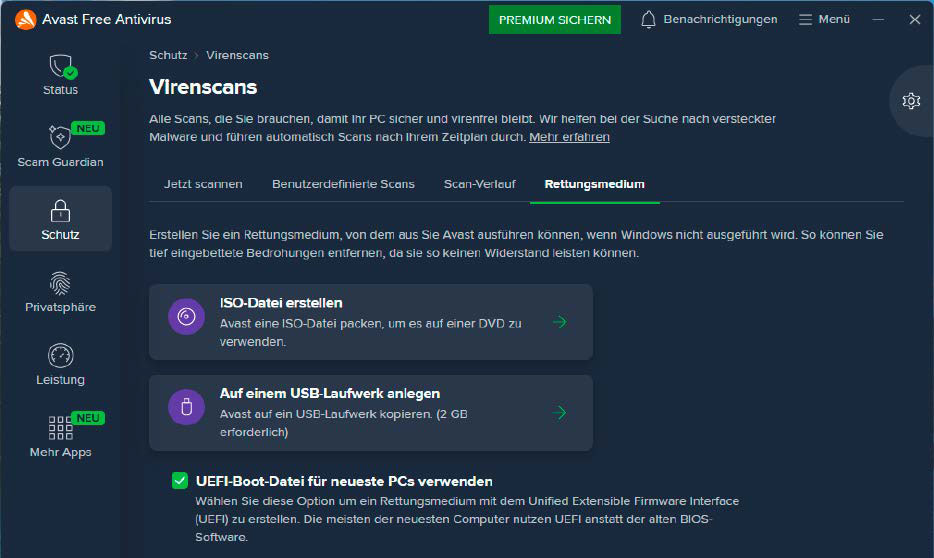
After putting in a further part, the Avast virus scanner presents to create a rescue disc on DVD or USB persist with an built-in virus scanner.
Foundry
Third, you may as well use Sardu. With this freeware you may create bootable USB sticks and DVDs and equip them with an antivirus software of your alternative.
For this function, Sardu offers hyperlinks to freely out there rescue methods from antivirus producers and presents to obtain the packages immediately and combine them into the stick or DVD.
Start suspicious packages safely
Another methodology of detecting false alarms is to run a suspicious program in a safe atmosphere.
This generally is a digital machine through which you put in Windows after which begin the software program to be analyzed.
If it brings a virus with it, it stays locked within the digital machine. As a rule, it isn’t potential to skip to your desktop Windows. You can subsequently take your time to look at whether or not it’s ransomware, for instance, which is now beginning to encrypt the digital SSD.
The different is to make use of a sandbox. This can be a shielded atmosphere that provides the malware no alternative to interrupt out. Online sandboxes similar to Any.run are straightforward to make use of, however you may as well use regionally installable sandbox software program similar to Sandboxie.
Caution: Many viruses are programmed in such a means that they solely develop into energetic after a interval of a number of hours, days, and even weeks. So if a program in a sandbox doesn’t initially present any abnormalities, this doesn’t imply that it’s actually protected.
Virus warnings as a lure
Especially in the dead of night corners of the web, browser home windows pop up repeatedly, reporting {that a} virus has allegedly been discovered in your PC. To clear up the issue, you must instantly conform to obtain an antivirus program.
Caution: These messages are invariably scams. The software program provided usually has no perform. However, it tries to steer you to pay for a license by repeatedly displaying notices.
Worse nonetheless, these packages usually comprise a virus themselves, making your PC a part of a botnet, for instance.
Related content material
This article initially appeared on our sister publication PC-WELT and was translated and localized from German.
