Passkeys beat passwords.
Not everybody agrees. But I’ve discovered that some dissent is rooted in a lack of information how passkeys work.
I don’t blame the skeptics. Passkeys are easy to make use of, however their technical nuances could be a headache to know. So let’s get into the small print.
What a passkey is
Passkeys are the casual identify for the WebAuthn customary for authentication. It depends on asymmetrical encryption (aka public-key cryptography). When you create a passkey, a public-private key pair is generated. The web site will get the general public key. You personal the personal key, which stays secret. It facilitates the authentication course of, however it’s by no means instantly shared for the verification course of to finish. Nor can or not it’s extrapolated from the general public key.
Your personal secret is tied to wherever you reserve it, with two most important choices for storage:
Cloud storage
Apple, Microsoft, and Google all can retailer each passwords and passkeys to your account.
PCWorld
Saving your half of a passkey to a cloud-based service affords probably the most flexibility—you possibly can entry it from any of your units.
For many individuals, this technique will occur by way of a Microsoft (Windows), Apple, or Google account. You can even choose to save lots of to most third-party password managers now, too.
Currently, you possibly can’t freely switch passkeys between cloud companies, however that ought to change within the coming months. Apple simply enabled porting (aka CXP) in iOS 26 and macOS 26, as has third-party password supervisor Bitwarden, which permits for safe import and export of each passkeys and passwords with different appropriate companies.
The most important benefit of cloud storage is comfort—once more, so long as you possibly can entry your account, you should use passkeys saved to it. But the drawback is that if anybody breaks into your account, they’ll use these passkeys, too.
Local storage

YubiKey
When passkeys first launched, these had been saved regionally to your cellphone or PC. You might additionally save them to a safety key like a YubiKey or Google Titan Security Key.
Nowadays, most passkeys saved to a cellphone or PC will get linked to no matter cloud account you’re signed into. If you need to save a passkey to a chunk of {hardware} that you’ve full management over, you’ll have to make use of a local-only password supervisor (like KeePassXC) on your PC or a safety key.
The benefit of native storage is {that a} dangerous actor wants entry to the {hardware} to get at your passkeys. On the flip aspect, the drawback is that for those who lose the system and don’t have any different passkeys or different strategies for login, you possibly can’t get into your accounts.
Roaming vs Platform Authenticators
I’ve outlined the methods you possibly can retailer a passkey in sensible phrases above—however bear in mind that the WebAuthn customary defines it in a different way. It distinguishes between “roaming” and “platform” authenticators. A safety key (e.g., YubiKey) is an instance of a roaming authenticator; you possibly can transfer it between totally different units. Devices like PCs and telephones are thought of “platform” authenticators—you received’t be shifting the passkey between units to be used.
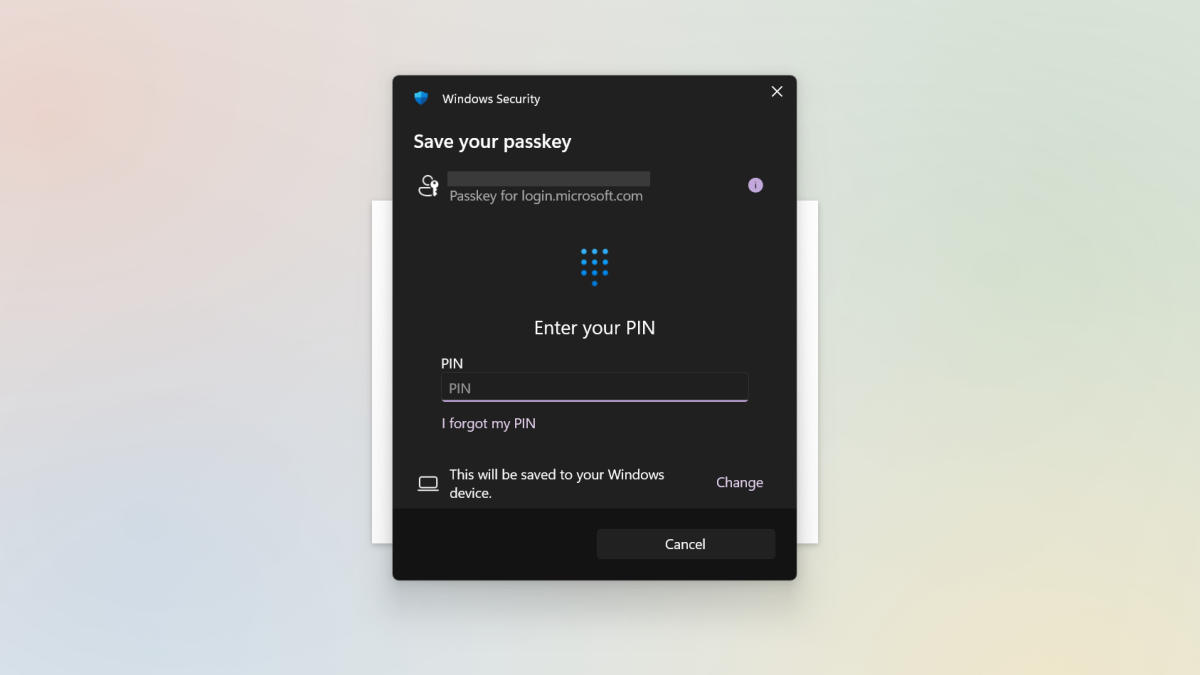
What a passkey is just not
Not restricted in use
PCWorld
Passkeys get tied to the service or system they’re created on—which has led some folks to imagine that they’re sure to ecosystems. (That is, Google, Apple, Microsoft, and third-party password managers all need to lock you into their service, since you possibly can’t but freely transfer the passkeys between them.)
But passkeys differ from passwords—you possibly can create a number of passkeys for a single web site (versus solely ever having a lone password). Think of it as just like a housekey. Each key for a selected lock can solely exist in a single place at a time (for this reason we will’t ever discover them after we want them…). But you possibly can have multiple key to open that lock. The distinction between a housekey and a passkey is that further housekeys are copies. Extra passkeys are distinctive and may’t be copied for use elsewhere, in order that they’re nonetheless safe.
So you might create a passkey for a selected web site on your Microsoft account, one other on your Apple account, and but a 3rd on your Google account, and all would work for logging in. You’re not really trapped into any a kind of ecosystems.
Not without end sure to a tool or service

Apple
At launch, passkeys had been particularly tied to no matter system or service they had been created for, which is why the flexibility to create a number of was so very important in making them usable.
In some methods, this was a safety characteristic—for those who had a passkey that would by no means be moved, then you definitely additionally by no means needed to fear about anybody with the ability to switch that non-public key away from you. (At least, in need of this XKCD method.)
That, nevertheless, solely utilized to regionally saved passkeys. If you had a passkey saved within the cloud, you continue to needed to be cautious that nobody gained unauthorized entry to the account it was saved to.
It additionally nevertheless was a ache within the butt for many individuals—if a tool together with your passkeys turned misplaced, stolen, or broken, you had been out of luck for those who didn’t have any backup passkeys or different login strategies arrange.
So now, the flexibility to securely switch your passkeys is rolling out.
Passkey vulnerabilities
Now let’s discuss vulnerabilities—and type out a few of the confusion I’ve heard folks categorical about how passkeys stack up towards passwords. In all of those situations, we’re assuming implementation is completed appropriately.
Phishing
Phishing will be outlined as an try and trick folks into sharing delicate info. It’s a broad umbrella time period and is available in totally different flavors, like social engineering and malware.
Simple phishing assaults merely ask on your credentials through emails, textual content messages, or calls from dangerous actors posing as respectable companies. More subtle ploys lure victims to pretend web sites masquerading as respectable. When login information is enter, the person ID and password get stolen. Even accounts with two-factor authentication aren’t all the time protected—that information will be grabbed in actual time, too.
Troy Hunt / HaveIBeenPwned
Experts say passkeys are phishing resistant for 2 most important causes. The first, an attacker can’t really steal parts that make up the passkey. The public secret is certainly public by design, and the personal secret is saved solely by you. They work collectively to create the piece of shared knowledge that completes the authentication course of, however they aren’t what’s exchanged. So nothing will be stolen (or used) in the identical means as a person ID and password.
Second, the usual additionally solely permits use of a passkey with the originating area. If a phony web site makes an attempt to trick you into utilizing a passkey for authentication, your browser will examine for the unique area linked to the passkey and shut down the try. The phishing area received’t match. You received’t have the ability to override this course of as you possibly can with password autofill, both. The authentication course of simply received’t start, and you’ll’t drive it.
Similarly, if an attacker locations a respectable login type inside an iframe, it shouldn’t work. For authentication to work when an iframe is in use, the handoff requires established coordination between the domains with a purpose to settle for the mismatch. While not unimaginable, a pretend phishing web site possible can not enact this implementation between its phony area and the official one.
Note: This info is present to now—attackers are all the time developing with new methods to discover a means round roadblocks reminiscent of these. The panorama might change with time.
Meddler within the center (MitM) assaults
In a MitM assault, hackers actually place themselves between you and the positioning you’re speaking with, in order that the info passes by way of them. So in a single variation of this assault, dangerous actors will steal your credentials whereas feeding them to the respectable web site—together with two-factor authentication codes. Afterward, the attacker has a viable session lively, and now not wants 2FA to start account takeover.
Passkeys shield towards this sort of credential theft, however not a variant generally known as session hijacking. More historically, session hijacking focuses extra on the thought of cookie theft, in order that an attacker can place the cookies on their very own system after which entry the account by way of the validated session.
Justin Morgan / Unsplash
Passkeys can’t shield towards this—which is why stopping malware in your system is essential. Website operators can mitigate this sort of assault by way of issues like tying the session to the system or locale, and many others. But that’s out of the passkey’s realm of affect. Once the authentication occurs, its job is over.
In concept, malware in your system might additionally mess with or tamper together with your browser’s skill to execute the WebAuthn customary as designed to, so once more, nonetheless finest to watch out about what you put in. But this isn’t a knock on passkeys—malware can simply as simply steal your passwords instantly out of your password supervisor, too.
One final passkey consideration
Overall, a passkey is safer than a password—and extra handy than utilizing a password plus two-factor authentication.
But the way you safe your passkeys might matter, if in case you have cause to suppose that your biometric knowledge isn’t protected. For on-line safety functions, your fingerprint or face will likely be safer than a PIN, which will be shared extra simply and broadly. But inside some jurisdictions (just like the United States), you possibly can’t be compelled to disclose a PIN to the federal government. Biometrics aren’t protected in the identical means.
For most individuals, such a distinction received’t be a priority. But for many who should weigh such issues, it’s value realizing.
