Linux is consistently evolving, and with it the instruments that its followers use each day. However, a number of the classics comparable to iptables , which has been changed by nftables , at the moment are not solely outdated, but additionally probably insecure or inefficient.
Yet they’re nonetheless referenced in lots of Linux books and on quite a few web sites. This tempts customers to proceed utilizing them.
In this text, we current essentially the most ceaselessly encountered “deprecated“, i.e. out of date, Linux instructions. Many customers are most likely nonetheless conversant in them. However, for the explanations simply talked about, they’re now not updated as a result of they’ve unclosed safety gaps, incomplete capabilities, or there are extra environment friendly options.
Some of the outdated instructions have already been faraway from the present distributions. However, others are nonetheless included.
The Netfilter challenge not solely takes care of the basic iptables, but additionally of its successor nftables, which additionally replaces the instructions ip6tables, arptables, and ebtables.
Foundry
Software developer and system administrator Jose Vicente Nunez, for instance, has compiled a list of Linux commands that should no longer be used for the Red Hat weblog.
He additionally names options which, in his opinion, provide a minimum of the identical vary of capabilities, are nonetheless normally extra highly effective and are additionally nonetheless actively maintained.
egrep and fgrep
Nunez cites the instructions egrep and fgrep as the primary examples. They’re primarily based on the grep instrument, which particularly searches for textual content patterns in recordsdata or inputs. However, each egrep and fgrep are now not being developed additional as a result of they’ve now been built-in into grep as extra parameters.
Instead of the stand-alone command egrep, which makes use of prolonged common expressions to search out the specified sample, now you can use
grep -EThis lets you use extra advanced patterns and particular characters with out having to masks them.
Similarly, fgrep has been changed, which searches for mounted, i.e. unchanged textual content strings and thus saves time. Today, the fgrep command primarily corresponds to
grep -FIn newer distributions, each egrep and fgrep are merely symbolic hyperlinks to grep.
nslookup
The nslookup command can be now not fairly updated. It was and remains to be ceaselessly used in the present day to carry out DNS (Domain Name System) queries.
For instance, it may be used to search out out the IP tackle for a website utilizing a ahead lookup or the area identify for an IP tackle utilizing a reverse lookup.
In addition, nslookup can be utilized to particularly question varied DNS servers, examine DNS entries or diagnose identify decision errors.
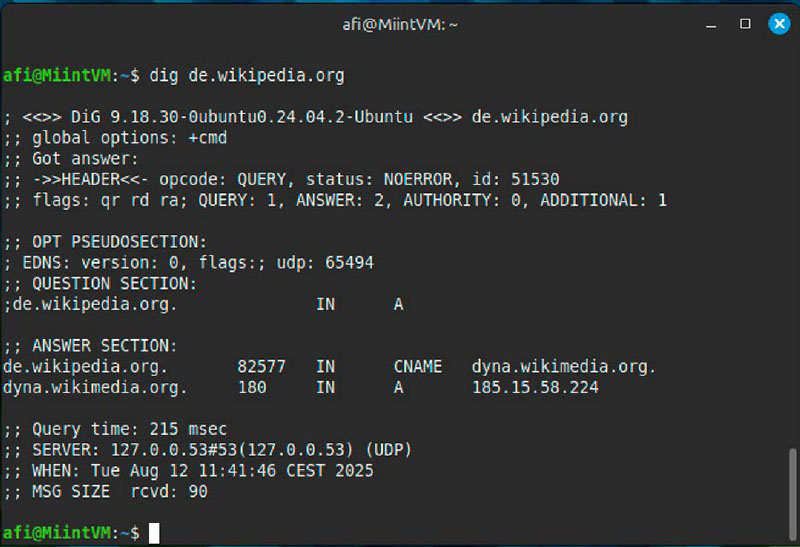
The dig command informs you that de.wikipedia.org is one other identify for dyna.wikimedia.org, shows the corresponding IP tackle and thus supplies a fast overview of the DNS mapping.
Foundry
The choice to cease creating nslookup was cancelled in 2004. Nunez and lots of others nonetheless advocate utilizing the instructions
digand
host instructions.
For instance, dig is a part of the BIND DNS instruments, that are actively maintained and might subsequently now do greater than nslookup.
The identify is without doubt one of the open supply neighborhood’s favourite puns. On the one hand, the time period “to dig” might be translated as “to dig up”, however it’s also the abbreviation for “domain information groper”.
Dig helps DNSSEC, can carry out focused queries of all document varieties, delivers structured and easy-to-read output and subsequently affords higher flexibility even for advanced queries.
In addition, in contrast to dig, nslookup doesn’t use the working system’s native area identify system resolver library to carry out queries. As a outcome, nslookup might return totally different outcomes than dig if, for instance, the resolver library takes extra “hosts” recordsdata into consideration or makes use of a neighborhood cache.
ifconfig, route and netstat
The ifconfig command is without doubt one of the best-known instruments that’s now not fairly updated. If this system is used with out parameters, it reveals the present community configuration. However, it may also be used to configure the community adapter along with data on the server tackle, gateway, netmask, or IP tackle.
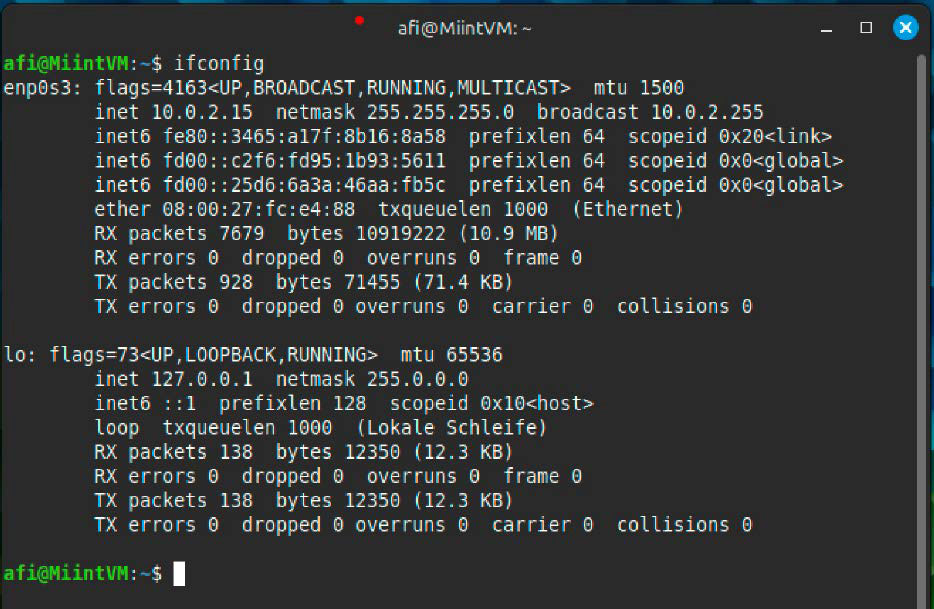
The Linux command ifconfig is without doubt one of the hottest relics from the previous, however the various ip affords much more choices and capabilities for exactly managing community interfaces, IP addresses, and routing.
Foundry
Most distributions nonetheless embrace ifconfig. The command ought to have been changed years in the past by the choice
ipfrom the iproute2 household.
At first look, ip seems extra difficult than ifconfig, as a command comparable to “ip addr show” is required to show the present IP tackle. Instead, ip supplies data with a command comparable to
ip hyperlink presentip supplies details about the community interfaces, comparable to actual or digital community playing cards and WLAN adapters.
Further examples of using the ip command:
ip hyperlink set eth0 upActivates the community interface “eth0”.
ip hyperlink set eth0 downDeactivates the community interface “eth0” once more.
ip addr present dev eth0Shows the IP tackle of the community interface “eth0”.
ip hyperlink present dev eth0Shows the main points of the community interface “eth0”.
ip addr del 192.168.0.77/24 dev eth0This command is barely out there with ip, for instance. It deletes the desired IP tackle for the interface “eth0”. In addition to such duties, ip additionally supplies details about the routing desk:
ip route presentor
ip route listingHere the ip command reveals the routing desk and thus additionally replaces the route command. The “route -n” command shows the addresses in tabular type, however solely numerically and with out DNS decision. The output of “ip route show” or “ip route list”, however, is much extra compact and incorporates extra data.
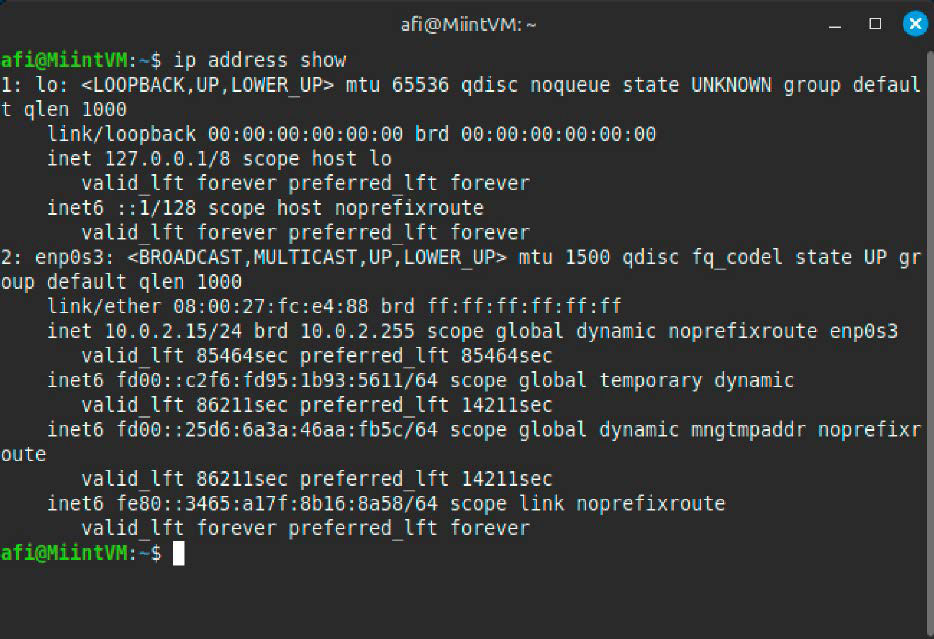
The ip command initially seems extra difficult than ifconfig, however supplies extra detailed details about the assorted community layers, for instance, and permits the community configuration to be managed and analyzed extra exactly.
Foundry
Another community command, which on this case is changed by the command
ss (the abbreviation stands for “Sockets Statistics”) is netstat. The instrument reveals, for instance, the listing of energetic community connections. An instance:
netstat --numeric --tcp --listenThe command lists the energetic TCP connections with out identify decision. The ss equal is
ss --numeric --tcp --listenThe ss command can be a part of the iproute2 package deal and replaces netstat on trendy techniques, as it might show extra particulars and likewise begins sooner.
While netstat retrieves data from the “/proc” recordsdata, ss accesses the kernel straight. In distinction to netstat, which is now not an actively maintained nettool, ss is constantly being developed and tailored to trendy working techniques and protocols.
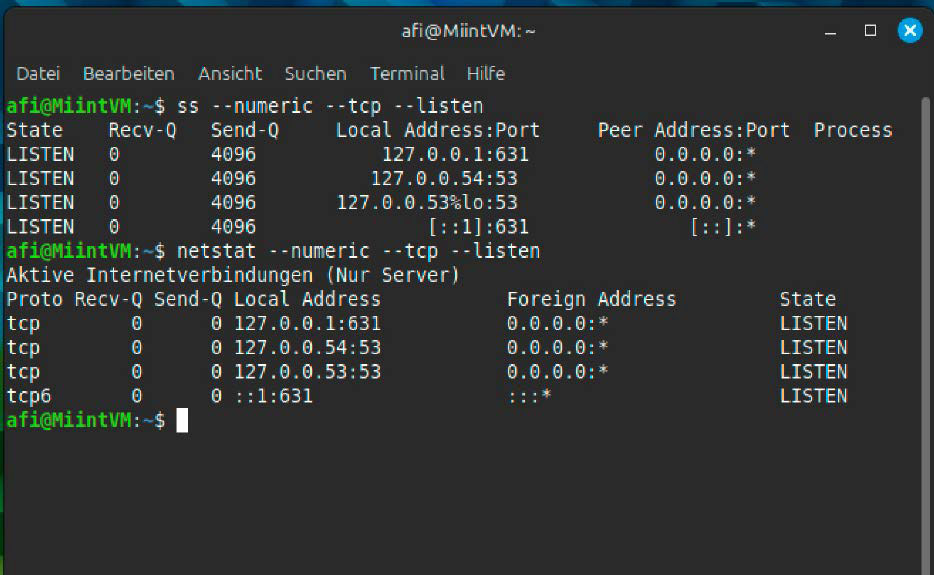
The netstat and ss instructions each listing the energetic TCP connections with out identify decision. ss works straight with the kernel and subsequently supplies extra particulars on sockets.
Foundry
The “ss” command with out additional parameters outputs an inventory of all community connections.
Another of the command’s strengths is that it might filter connections in accordance with varied standards. For instance, “ss -t” solely lists TCP connections, whereas “ss -u” does the identical with UDP connections. To show which processes are accessing the community, use the command “ss -p”.
iwconfig
Another community command that’s now thought of out of date for good cause is iwconfig. It is just like ifconfig, however is designed for wi-fi adapters. It can nonetheless be present in some distributions comparable to Ubuntu. However, others comparable to Red Hat have already eliminated it and changed it with the newer
iw command.
This is as a result of iwconfig doesn’t cowl many present WLAN capabilities and now not reliably helps trendy requirements comparable to 802.11ac or 802.11ax.
Iw, however, is being actively developed additional, supplies detailed details about community playing cards, sign strengths, frequencies and channels, permits advanced configurations, and helps all present WLAN requirements in addition to new capabilities comparable to mesh networks or WPA3.
scp
The scp command is one other basic, however its use is now not advisable. One of its strengths is that it’s just like the well-known cp command, which can be utilized to repeat recordsdata and directories regionally on a pc.
Scp, however, is used to switch encrypted knowledge over the community utilizing SSH (Secure Shell). In addition to cp, scp additionally incorporates capabilities for authentication with a password or SSH key.
For instance, the command
cp report.txt /house/person/backup/copies the file “report.txt” from the present listing to a backup folder. With scp it might appear to be this:
scp report.txt person@server:/house/person/Instead of simply specifying a neighborhood path, scp requires just a few extra particulars. For instance, “user” is the person on the distant system, “server” is its tackle and “/home/user” is the trail to the listing to which the “report.txt” file is to be transferred.
Another distinction is that the switch solely takes place after the proper password has been entered. With each variants, it’s also doable to append a file identify to the trail. The instructions then change the unique file identify to the brand new one.
In the article “Deprecating scp“, the creator Jonathan Corbet describes a very powerful explanation why scp is now not being developed additional.
Jonathan Corbet explains on LWN.web the explanation why even long-time scp customers ought to now not use this system to switch recordsdata over the community.
Foundry
For instance, scp relies on the outdated rcp protocol, which is now classed as insecure. Another drawback, in accordance with Corbet, is the tactic utilized by scp to cross arguments. This may result in the unintentional execution of instructions, particularly on techniques on which entry is definitely restricted to easily copying knowledge by way of scp.
Red Hat and Fedora have subsequently determined in 2022 to now not assist the outdated SCP protocol by default. The scp command remains to be out there, however now makes use of the safer SFTP protocol internally by default (relying on the interpretation, the abbreviation stands for “Secure File Transfer Protocol” or “SSH File Transfer Protocol”), whereas the reference to the unique SCP protocol has been eliminated.
The cause given by Dmitry Belyavskiy, Senior Software Engineer at Red Hat, is that the SCP protocol is already a long time outdated and has quite a few safety dangers and issues for which there aren’t any easy options.
The change was programmed with the involvement of Jakub Jelen, who was energetic as a maintainer for the Open SSH package deal for a number of years. As a precaution, nonetheless, a sort of backdoor was in-built.
There is now the brand new scp swap “-O”, which reactivates the outdated SCP protocol. However, it’s more likely to be eliminated once more in one of many upcoming Red Hat releases. Its use is subsequently not advisable.

With the discharge of RHEL 9, Red Hat has determined to not take away scp fully, however to switch the underlying protocol with SFTP.
Foundry
It subsequently makes extra sense to change to the options
rsyncor
sftp options. Both additionally use SSH to securely entry distant machines. Both additionally provide extra capabilities and, above all, are being actively developed additional.
iptables
Many Linux customers make the most of the iptables instrument for packet filtering and firewall configuration. It can be utilized to outline guidelines that permit, block, or redirect packets.
However, iptables is now additionally thought of outdated, primarily as a consequence of issues with scalability and efficiency.
For this cause, the Netfilter challenge itself, which additionally maintains the iptables userland instrument along with the kernel subsystem, is creating
nftables as a result of the iptables framework has turn out to be considerably complicated.
For instance, it’s not precisely environment friendly to create guidelines for IPv4 with iptables and for IPv6 with ip6tables with a purpose to then painstakingly synchronize them. This is simpler with nftables.
Both instructions work comparatively equally, however nftables not solely makes use of an easier syntax. The new instrument even understands the syntax of iptables. In addition, iptables- translate is one other instrument that converts iptables instructions into their nftables equal.
Conclusion: Please swap!
In the Linux world, modifications are typically moderately cautious. Outdated utilities typically stay in use for years, even when extra trendy and safe options have lengthy been out there. Only after an extended time period, typically solely after a number of years, are these older instruments step by step changed by their up to date counterparts.
However, this course of additionally ensures stability and compatibility within the Linux neighborhood. Many outdated instruments subsequently intentionally stay within the distributions for compatibility causes, however ought to a minimum of get replaced by their extra trendy options in tutorials, scripts, and new tasks.
