1. What is search parameter injection?
Search parameter injection assaults are a brand new, subtle technique utilized by criminals to acquire your knowledge and even achieve entry to your PC.
Criminals place adverts on Google which might be displayed each time somebody searches for the phrase “support” and a selected firm, akin to “support Netflix.” The advert seems straight above the primary search hit and is designed to look as if it comes from Netflix itself.
Anyone who clicks on this advert is — and that is the particular factor about this rip-off — not directed to a pretend web site, however to the unique Netflix help web site. However, the attackers have entered their very own phone quantity within the search operate on the help web page (see picture).
Here, criminals have inserted their very own phone quantity on the actual Netflix help web site. Anyone who calls there reveals their knowledge and, within the worst case, dangers catching a Trojan.
Foundry
A sufferer who calls this quantity then reveals their knowledge to the criminals, such because the password for the Netflix login. In some instances, victims are additionally persuaded to put in what seems to be help software program.
However, that is really a Trojan that provides the attackers entry to the PC.
Not solely Netflix is affected by this rip-off; the web sites of different massive corporations akin to HP, Dell, and others are additionally hijacked by the criminals.
How to guard your self: Many safety suites supply an online filter for the browser. This ought to acknowledge such assaults. The present malware marketing campaign was found by the antivirus specialist Malwarebytes. The Malwarebytes web site filter ought to due to this fact reliably block these assaults.
2. Is Defender sufficient?
The Microsoft Defender antivirus program is built-in into Windows as commonplace. It is free to make use of, it updates itself routinely, and the combination with Windows couldn’t be nearer — in any case, the device comes from the Windows producer itself.
In addition, Microsoft Defender’s virus detection has nearly at all times carried out very properly in previous checks. Defender is due to this fact adequate for any IT-interested person who has a wholesome stage of distrust in the direction of emails and web sites.
However, anybody who’s in no way concerned about IT safety and has by no means heard of phishing emails and harmful web sites is best suggested to make use of a complete antivirus suite, as this affords extra extra safety features.
Further studying: Best antivirus software for Windows
3. Are passkeys actually safer?
Passkeys are the brand new superstars relating to safe login to on-line companies. Instead of authenticating your self with a password, you use a passkey.
This is saved on a appropriate machine (any present smartphone or laptop) and launched utilizing fingerprint, face scan, or PIN authentication (Windows Hello). As there is no such thing as a password when logging in with a passkey, it can’t be stolen. Passkeys additionally present superb safety in opposition to phishing assaults.
So: Yes, passkeys are way more safe than passwords. Wherever potential, it is best to use passkeys to log in to a service.
However, if you happen to lose your smartphone, additionally, you will lose your passkey. In such a case, it’s troublesome for a web based service to reliably determine a person. In different phrases, to grant them entry to their account once more. That’s why there are only some companies that permit you to authenticate your self utilizing a passkey solely. There remains to be a password for logging in.
One exception is the Microsoft account, which can be utilized with no password as of this yr. In addition, the usage of passkeys shouldn’t be as easy as many individuals suppose. There are issues, for instance, when you have saved passkeys each within the working system (akin to Android) and in a password supervisor.
4. How do I defend myself from crypto miners?
Crypto miners are malware that use your PC to calculate digital cash. The risk is available in two types:
- First, as basic malware that embeds itself in your laptop. You can block this malware with good antivirus software program.
- Second, crypto-miners lurk on the net: Javascript-based mining is embedded on ready web sites, which turns into energetic straight when the web page known as up. In this case, the malware solely runs whereas the browser session is open and disappears when the web page is closed.
How to guard your self: To stop mining within the browser, use the Opera browser for unknown and presumably contaminated web sites. It routinely blocks mining code.
5. How harmful are AI assaults?
Artificial intelligence creates convincing texts, cloned voices, pretend movies, and useful program code inside minutes. It finds safety loopholes in software program and server companies and is extraordinarily cheap. Cyber criminals additionally benefit from this.
However, the query of how harmful AI assaults are in consequence varies. However, there are some consultants who anticipate a flood of extraordinarily harmful assaults within the coming years.
Below are a couple of concrete examples of how AI is altering cyber assaults.
Artificial intelligence improves present assaults and makes criminals’ work simpler. While phishing emails may nonetheless be simply distinguished from real emails with a little bit suspicion, among the present phishing emails created with AI seem deceptively real. This signifies that they’ll hardly be distinguished from real emails by way of kind and content material.
A free device can be utilized to exchange a face in a stay video. Another device may also be used to exchange the voice.
DeepFaceLive
Internet customers are additionally threatened by so-called deepfakes. These are, for instance, movies with well-known personalities, akin to a newsreader. However, this particular person shouldn’t be studying the information on a web site, however is as a substitute promoting doubtful cryptocurrencies and shares.
What’s extra, assaults of this type are a lot quicker these days, as new AI instruments are serving to the criminals. These instruments are known as FraudGPT, WormGPT, AI Phish, or ScamGPT. They generate new assaults inside minutes, which might in any other case have taken the criminals days.
How to guard your self: It helps to fastidiously verify the sender tackle and the hyperlinks contained in improved phishing emails. You can discover extra info on this in our guide.
To fight deepfakes, it helps to be suspicious and take a really shut take a look at the photograph or video in query. You can learn how to acknowledge the rip-off in our guide to deepfakes.
In the next information, however, we present you tips against attacks with fake voices.
6. Why are zero-day vulnerabilities so harmful?
A zero-day vulnerability is a beforehand unknown safety gap in software program or an working system for which no replace is but obtainable. The time period “zero-day” refers to the truth that the producer had zero days to react to the found vulnerability. Either it has not but been reported or it’s already being actively exploited.
At the identical time, vulnerabilities in software program — at the least if they’re severe vulnerabilities — are an actual boon for hackers. This is as a result of they’ll use them to realize entry to the system with out having to trick the person.
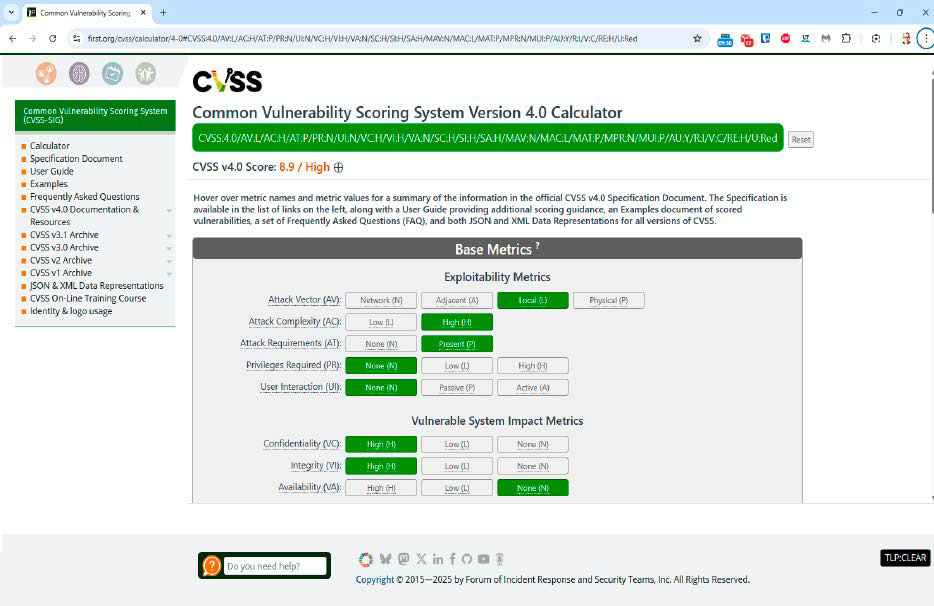
The CVSS 4.0 calculator reveals how harmful a vulnerability is in response to the Common Vulnerability Scoring System, and on the similar time how excessive the danger is that will probably be exploited.
Foundry
How to guard your self: The software program itself can’t defend itself in opposition to zero-day vulnerabilities, because the corresponding replace remains to be lacking. However, the heuristics of antivirus software program can often acknowledge the malicious code.
In the case of high-risk zero-day vulnerabilities, nonetheless, it could even be essential to disconnect the affected system from the web till an replace in opposition to the vulnerability is offered.
7. Where can I discover a web based virus scanner?
In reality, there are now not any on-line virus scanners that may scan your total laborious drive for malware. One of the explanations for that is that code from the browser now has considerably fewer rights on the PC than round 20 years in the past, when many on-line virus scanners labored by way of ActiveX within the browser. However, as we speak’s browsers now not supply ActiveX help.
The time period “online virus scanner” has survived, however what you get as we speak below this identify are easy antivirus packages. They are downloaded to your PC as an .exe file. Some should be put in, others begin with out set up. As a second opinion to the results of your already put in antivirus program, they’re definitely justified.
Examples of such virus scanners come from Eset, Trend Micro, and F-Secure.
Under the time period “online virus scanner,” there are additionally web sites the place a restricted variety of suspicious information could be uploaded. These are then analyzed to find out whether or not they’re harmful.
The best-known consultant of this kind is VirusTotal, which scans a file with over 40 antivirus instruments. The service is at all times price a go to when you have a suspicious file in entrance of you.
8. Can I get well information encrypted by ransomware?
There are appropriate decryption instruments for a lot of ransomware viruses. However, discovering the fitting device is often not straightforward, because the ransomware virus doesn’t disclose the code used.
You can discover assistance on the web site www.nomoreransom.org. A wizard will information you thru a course of on the finish of which, if all goes properly, you can be provided a decryption device in your information.
If you don’t discover something there, strive ID Ransomware. If no assist is obtainable there both, it is best to hold the encrypted information and verify once more in a couple of months.
Security researchers typically crack the encryption codes of ransomware solely after a while, or the criminals publish the grasp key — at the least this has occurred prior to now.
9. How do I defend myself in opposition to ransomware?
Ideally, dependable antivirus software program ought to acknowledge and block ransomware earlier than the malware turns into energetic and may encrypt private knowledge. However, even trendy safety options don’t supply 100 p.c safety.
The best safety in opposition to ransomware is due to this fact an up-to-date and externally secured backup. See our roundup of the best backup software for Windows to be taught extra.
Windows 11 has additionally provided special protection against ransomware for a number of years.
10. Are my information secure within the cloud?
Cloud storage shouldn’t be safe, however it may be made safe. There are a number of threats to delicate knowledge within the cloud: Hackers can achieve entry to the cloud. The cloud supplier has entry to the information, as do authorities companies.
The cloud supplier may also lock you out of your account, for instance if they believe that you’ve violated the principles. Something that has reportedly occurred extra continuously at Microsoft this yr.
How to guard your self: You can defend your self in opposition to espionage with good end-to-end encryption. We advocate the Cryptomator device, for instance. There are apps for Android and iOS in addition to instruments for Windows, Linux and Mac OS. The Windows software program from Cryptomator is donationware. The Android and iOS apps value 19 euros every.
The finest strategy to defend your self from being locked out of a cloud account is to create a backup of your knowledge by yourself PC. This could be arrange fairly simply with the Cryptsync device, for instance.
